ACL & NAT Changes in Sandbox
The Sandbox capability is an experimental functionality. The capability is ONLY limited to ACL, NAT and Firewall rules and ONLY on supported platforms.
Routing changes are NOT supported.
ACL & NAT changes in Sandbox enable network teams to model the correctness of changes before they are deployed to productions. Configuration changes to a network are typically tested in a lab environment. Such labs can never match the full scale and end-to-end behavior of a production network. ACL & NAT changes in Sandbox enable the user to “sandbox” a new version of the network model containing proposed changes, and instantly verify the effects of their changes on the existing compliance and security policies defined by the user.
Steps for ACL & NAT changes in Sandbox
- Enter in edit mode by clicking the Edit in Sandbox button.
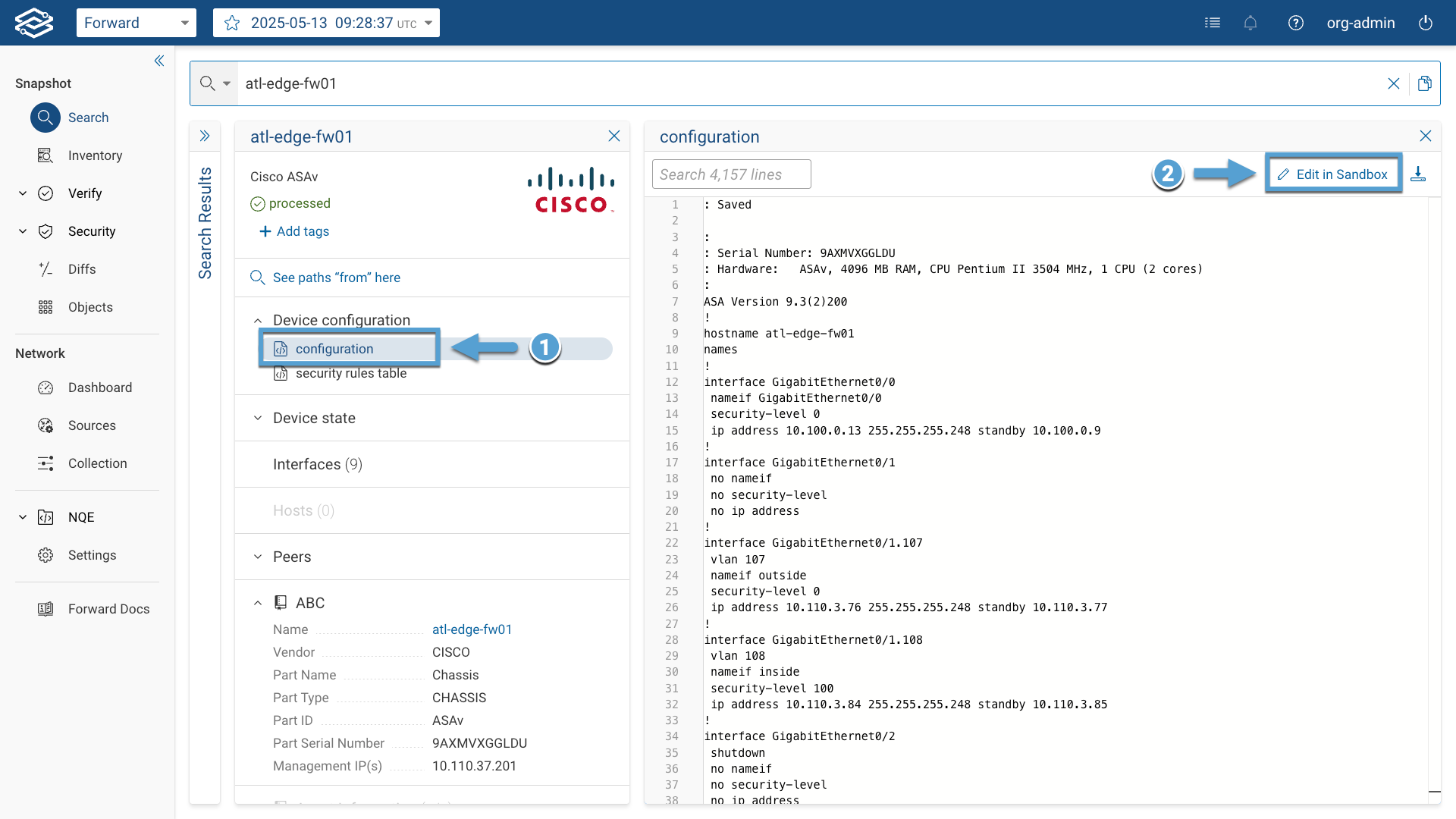
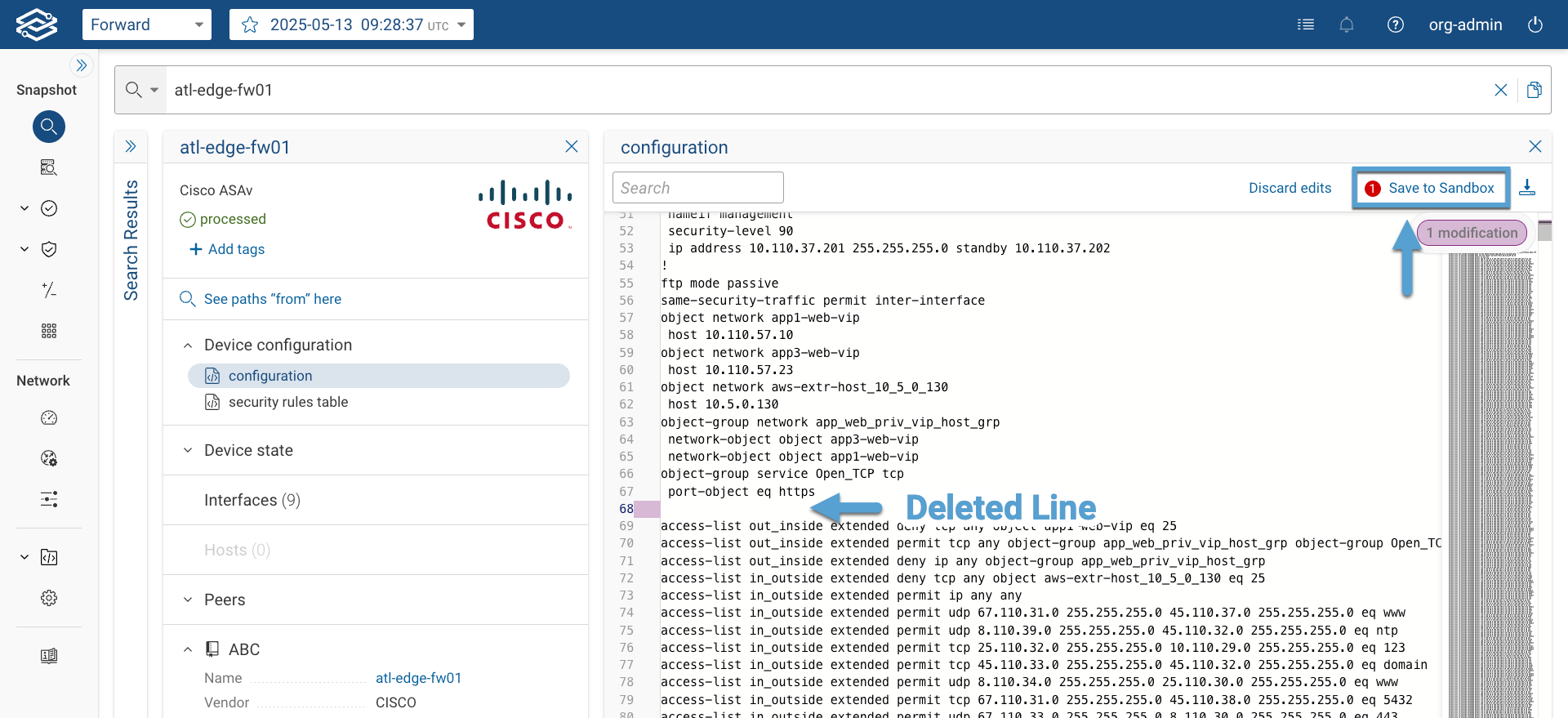
- Edit the device configuration and clicking on Save to Sandbox. Repeat the same process for every device configuration you want to change.
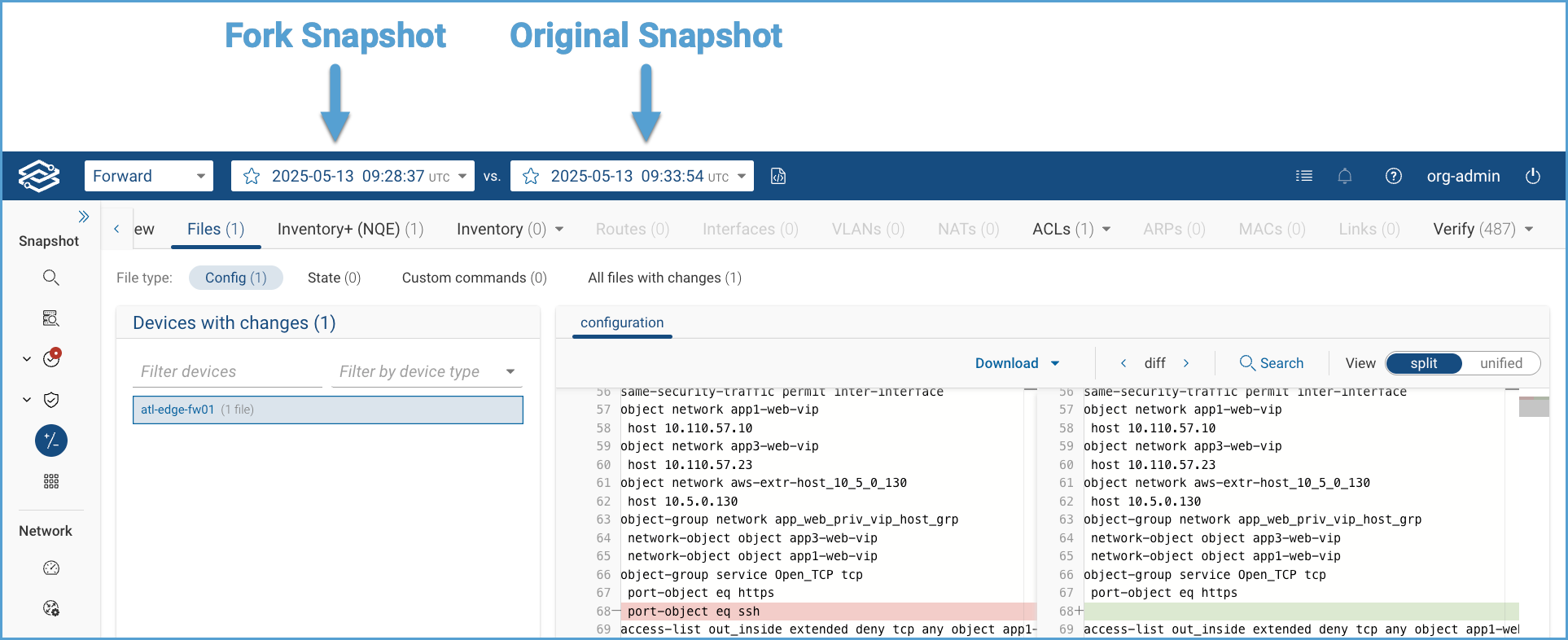
The system will try to parse the manually-edited configuration. The editor does not check for syntax errors.
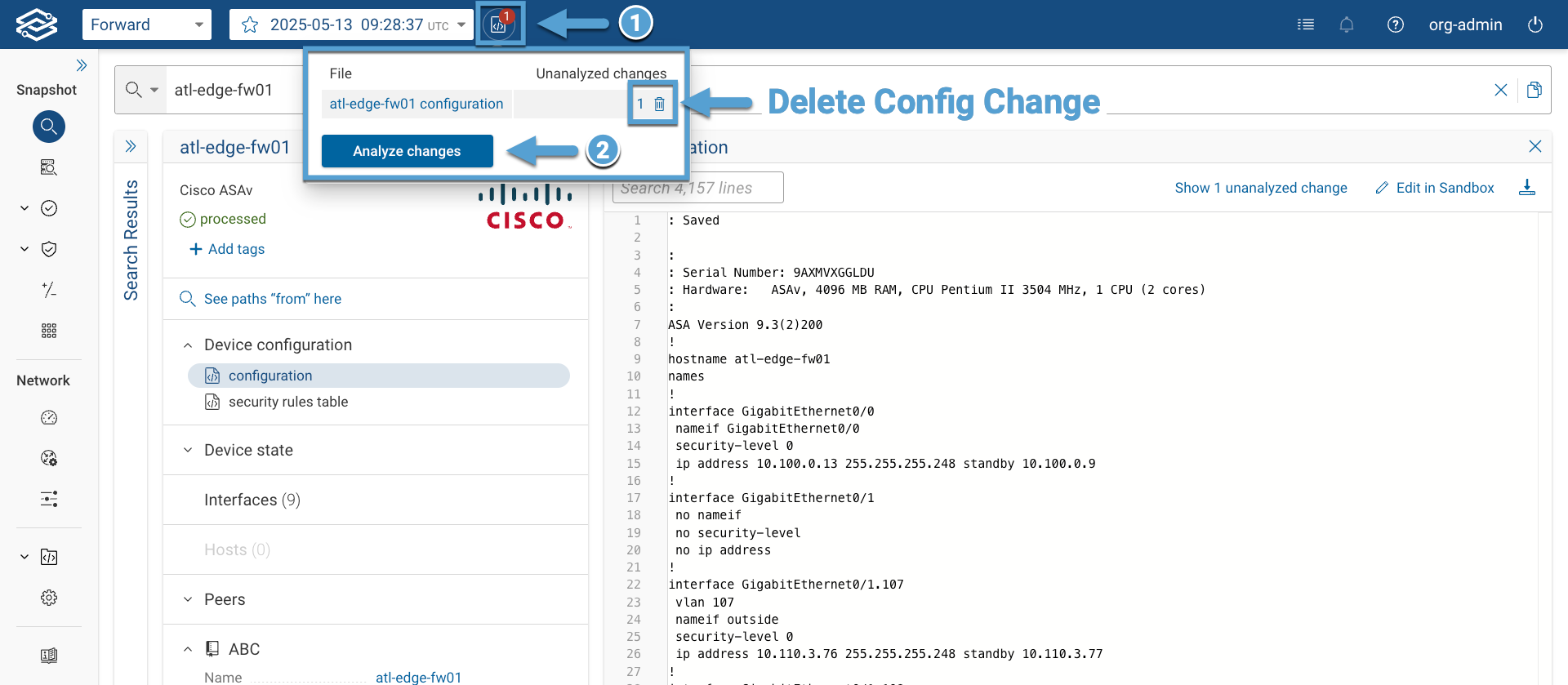
- Analyze the changes by clicking on the Analyze Changes button.
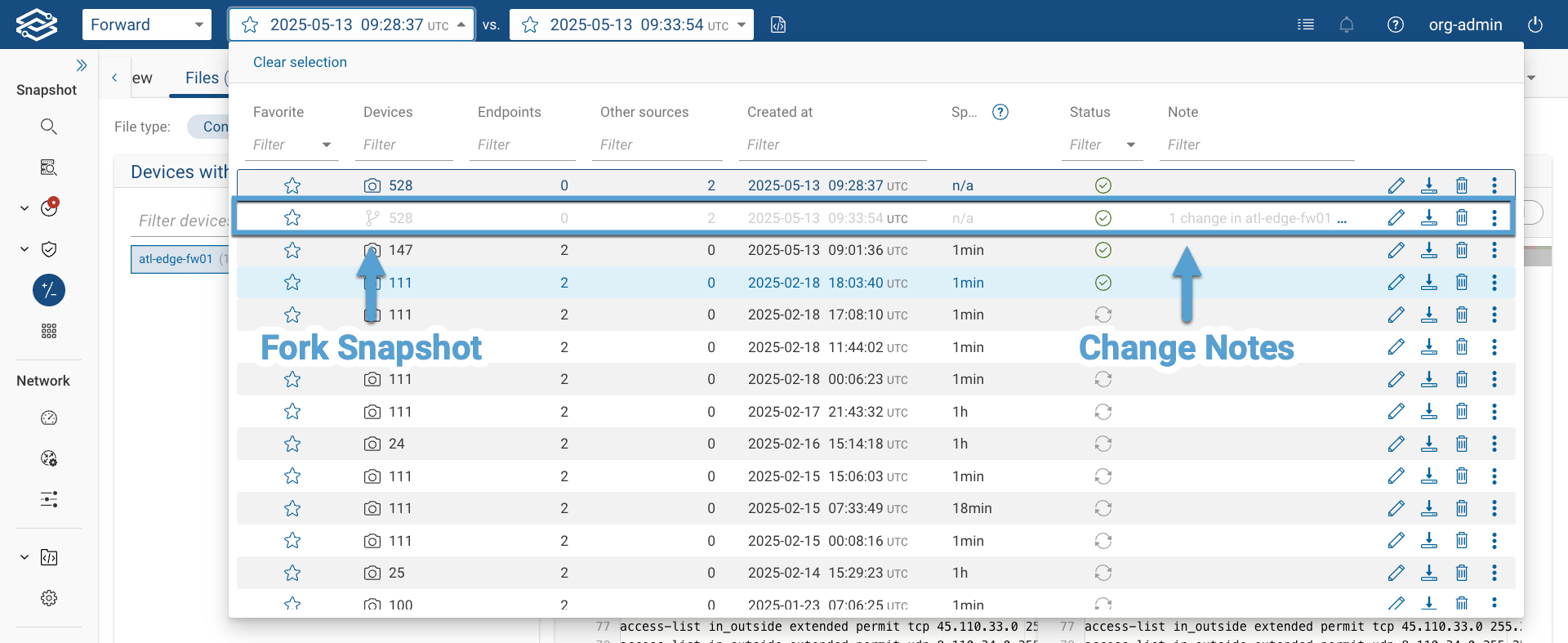
The system will elaborate the changes and create a new Fork Snapshot, and then show a before/after comparison for all verification checks
Supported Platforms
| Vendor | Support (Config Only) |
|---|---|
| Cisco (including ASA firewalls) | Yes |
| Arista | Yes |
| Juniper (including SRX firewalls) | Yes |
| Palo Alto Networks | Yes |
| Fortinet | Yes |
| F5 | F5 ltm No, f5 afm Yes |
| Cumulus Networks | Yes |
| HP | Yes |