Blast Radius
Forward Enterprise Blast Radius provides a comprehensive analysis of all reachable hosts or subnets from any source location or entity in the network.
In the event that a host is compromised, security teams need to understand how an attacker can move laterally from that compromised host to other hosts in the network. The Blast Radius application provides an understanding of how traffic can flow from the source to any host or subnet in the network including information on specific IP protocols, Layer 4 ports, and Layer 7 App IDs.
The Blast Radius application can also be used to comprehensively analyze which hosts are reachable from the Internet, a specific security zone, a network device, etc.
This comprehensive analysis empowers network and security professionals to evaluate the impact of compromised sources within the network. This understanding aids in assessing the security vulnerabilities of a potential attack.
Starting a Reachability Search
To get started, navigate to Security > Blast Radius and provide the following information within the Reachability Search panel:
- Source: Define the source, which can include devices, hosts, interfaces, security zones, device VRFs, device aliases, host aliases, interface aliases, and source subnets. Selecting Add Source provides additional Source fields to add additional sources.
- Destination Subnets: Specify one or more private or public destination subnets or individual host addresses for the analysis. This field supports both IPv4 and IPv6 addresses. Use post-NAT addresses when applicable. A /32 address can be used to define a specific host, while 0.0.0.0/0 allows reachability analysis to any destination.
- Include Non-host Targets: By default, the Blast Radius analysis returns only end-hosts discovered by Forward as reachable targets. Enable this toggle to return entire subnets that are reachable out of some edge ports in the network, not just discovered hosts.
- IP Protocol Exclusions (optional): Exclude one or more protocols by name (e.g., ICMP) or protocol number (e.g., 1).
- Search Timeout: Set the timeout duration for the blast radius computation in seconds (Default: 30 seconds).
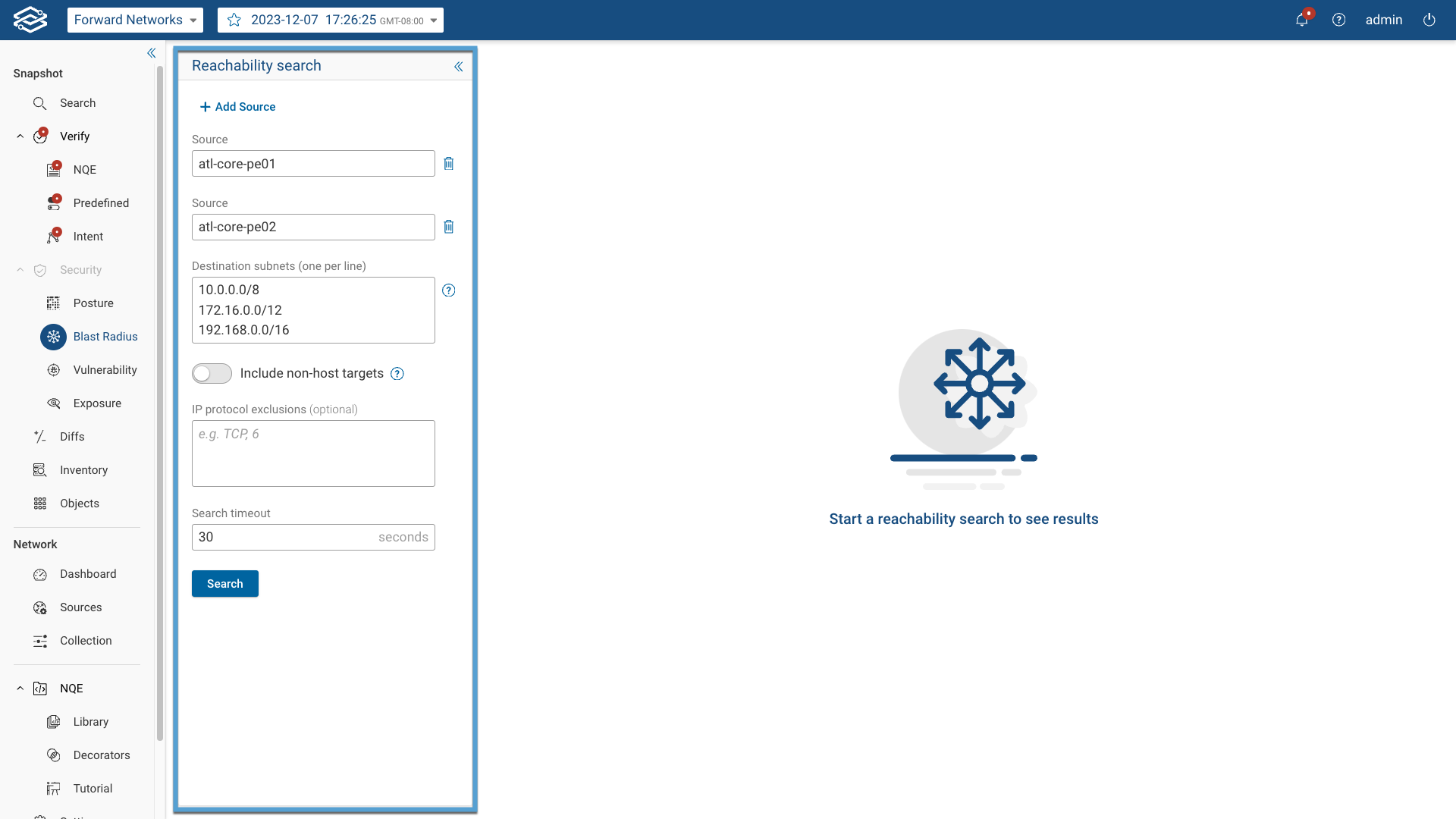
Select Search when ready to start.
Source Locations
The Source Location panel displays all of the sources used in the search, selecting a source from this panel will display the results for the selected source.
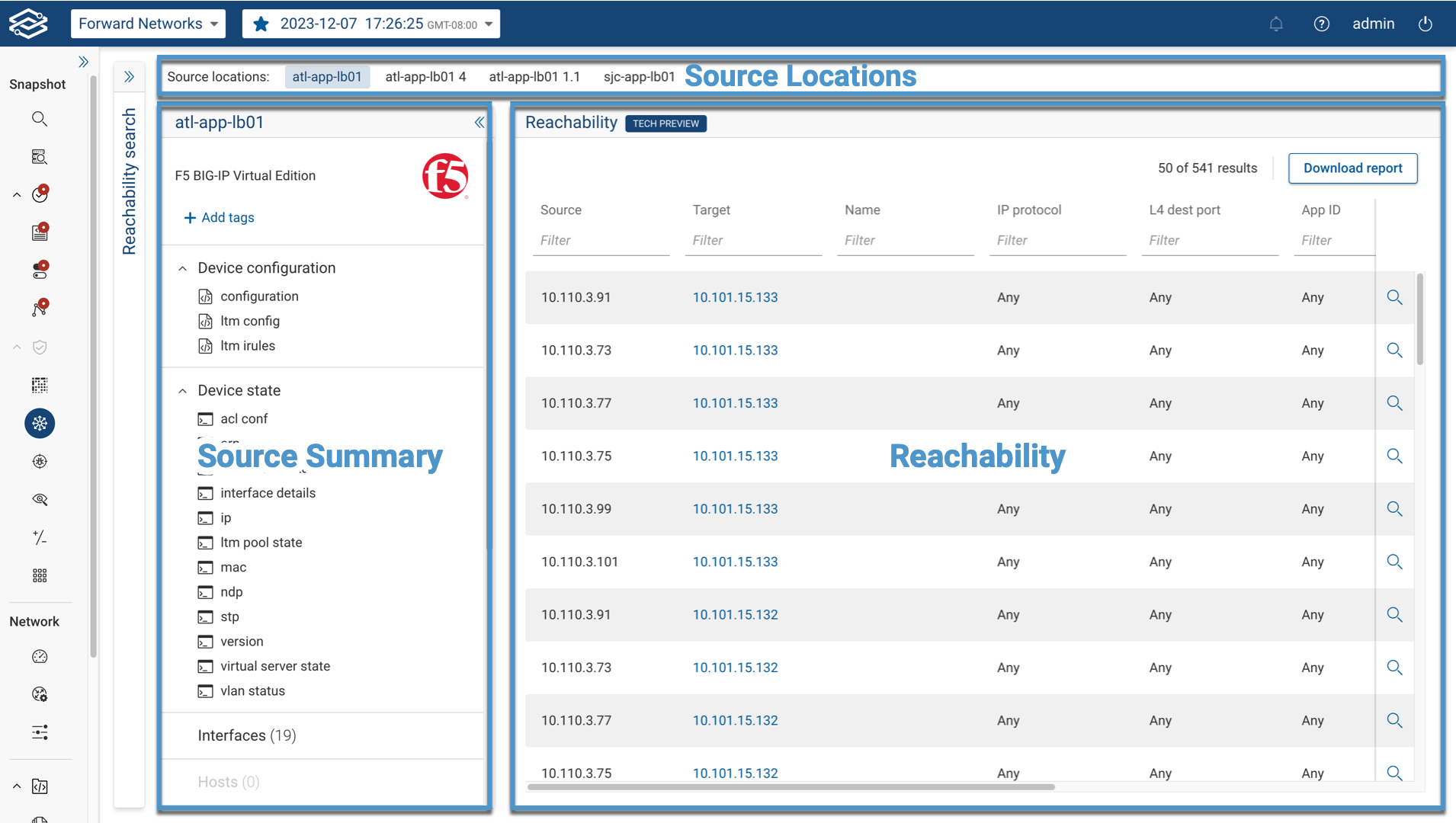
Source Summary
The Source Summary panel offers a detailed overview of the source based on its type. Additional information may be provided depending on the source type.
Reachability Results
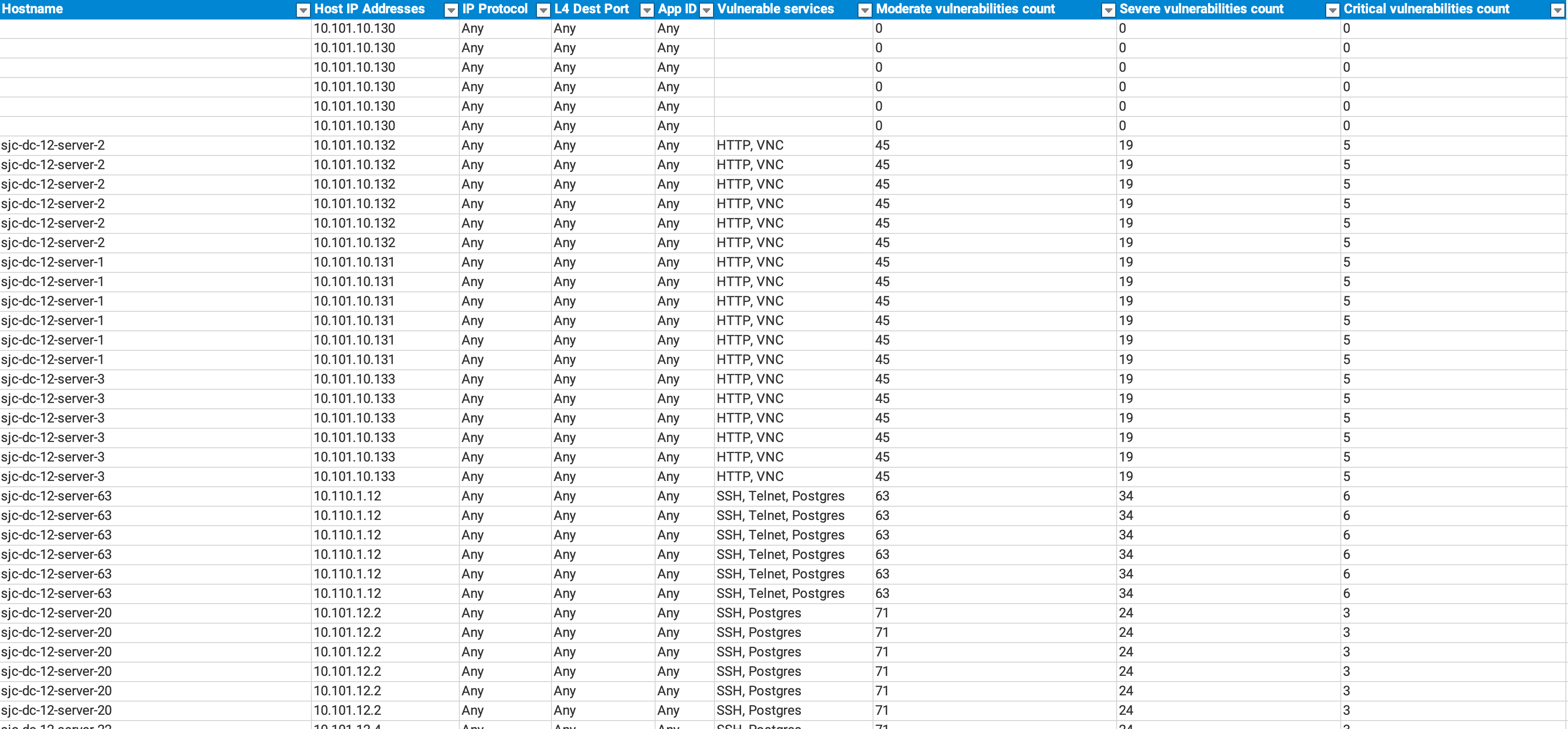
The Reachability panel provides a detailed list of all end-host targets reachable from the source. Each row includes the following columns:
- Source: IP addresses of the source.
- Target: IP addresses of the end host reachable from the source.
- Name: End hostname, if available.
- IP Protocol: IP protocols accessible by the source.
- L4 Dest Port: Layer 4 Destination ports accessible by the source.
- App ID: Layer 7 App IDs accessible by the source.
- Vulnerable Services: List of vulnerable network services accessible by the source.
- Critical: Number of critical vulnerabilities detected.
- Severe: Number of severe vulnerabilities detected.
- Moderate: Number of moderate vulnerabilities detected.
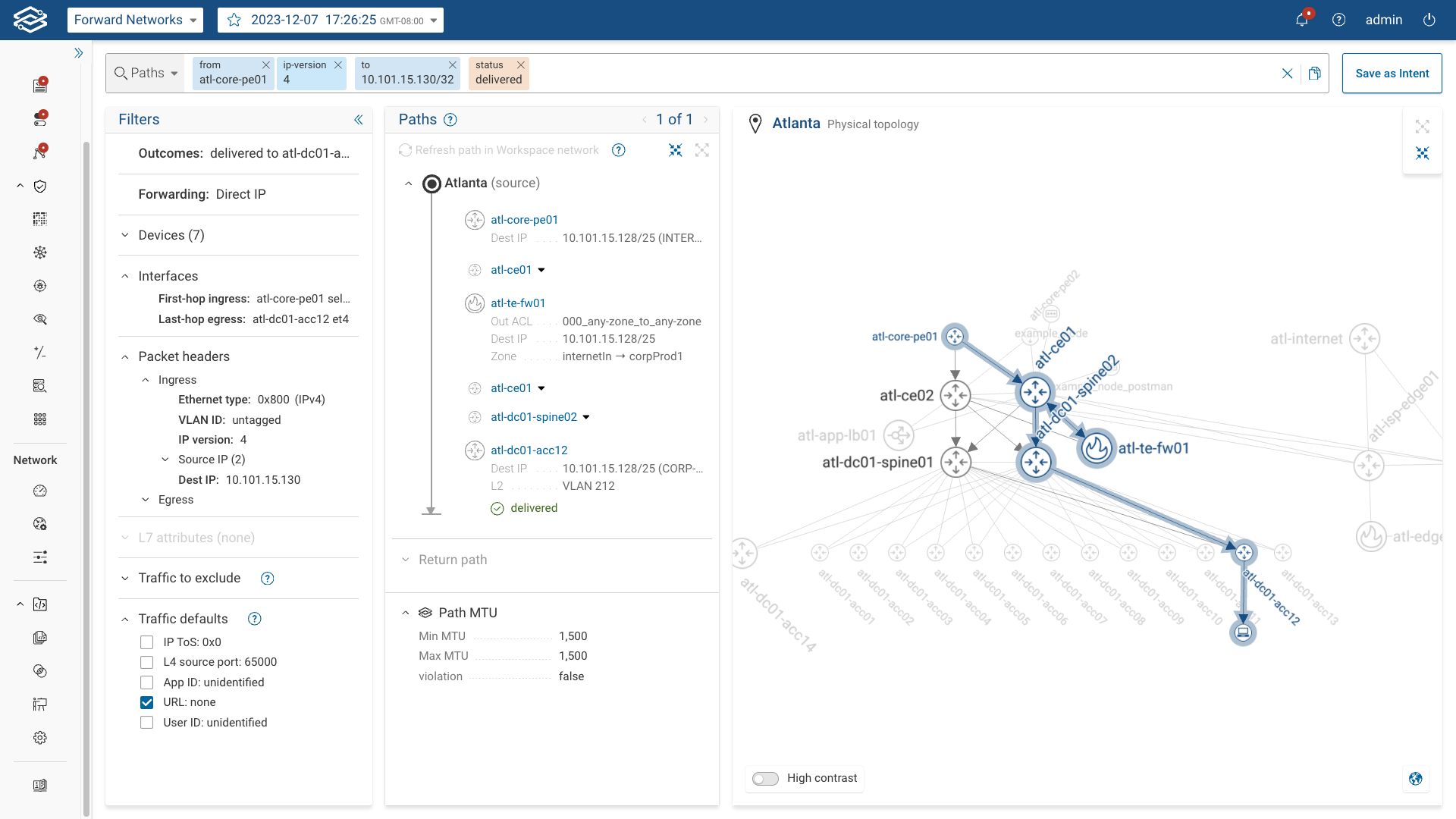
At the end of each row is View Sample Path icon, providing the path analysis results for each respective target for the given IP Protocol, L4 Dest Port and L7 App ID.
Downloading a Report
Selecting Download Report within the Reachability panel provides a report of the search results in an XLSX format.