Security Posture Analysis
Overview
Networks are usually segmented into zones and security policies between zones are implemeted to keep the environment secure. Examples of commonly used zones include DMZ, Guest, Production, Marketing, Engineering, etc.
The security policies may either completely block connectivity between the zones, allow partial connectivity for certain IPs and ports, or permit open connectivity without restrictions. It is also possible that the zones do not route traffic between them.
Forward Enterprise Security Posture Analysis gives users a complete and accurate picture of the connectivity status between zones in a visually consumable way, and it's updated every time a new network collection is taken.
How to create a new security matrix
Upon visiting the Security-->Posture page for the first time, a Sample Matrix is presented to the user indicating connectivity between a few sampled zones in the network.
New customized security matrices can be created using a simple wizard-based process that allows you to granular definition of each zone. Forward Enterprise allows you to define new zones as a pool of resources like VRFs, on-prem and cloud subnets, cloud security groups, and security zones.
Click on Add new matrix to open the drawer to create a new matrix. Provide a Matrix name, optionally, add one or more protocol exclusions either by protocol name (e.g. ICMP) or protocol number (e.g. 1) and click on Add resource pool to start the wizard to add resource pools one by one.
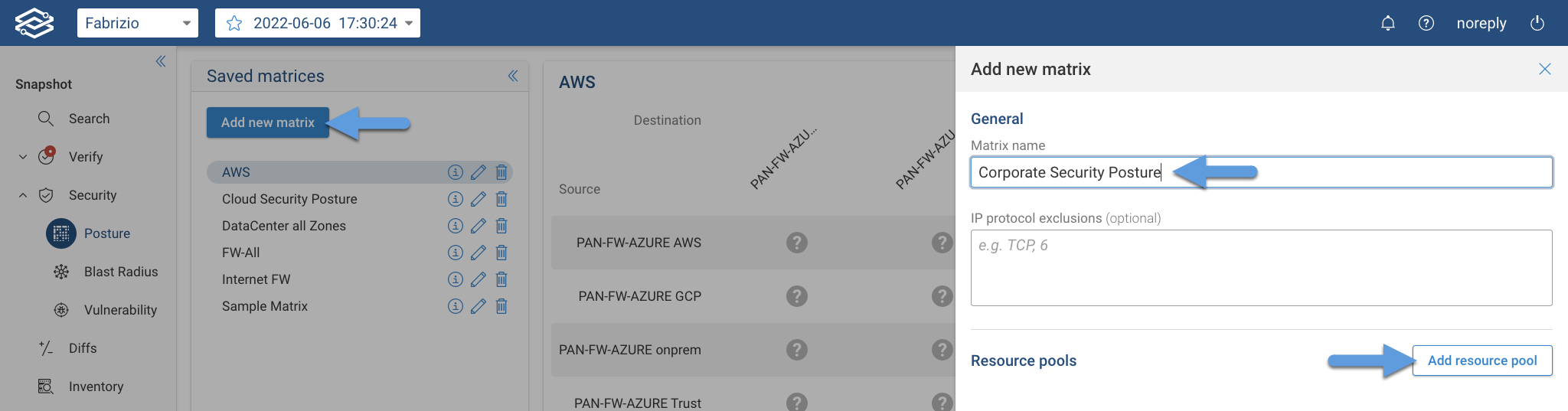
There are 3 resource pool types to choose from, On-prem, Cloud and, Security zone:
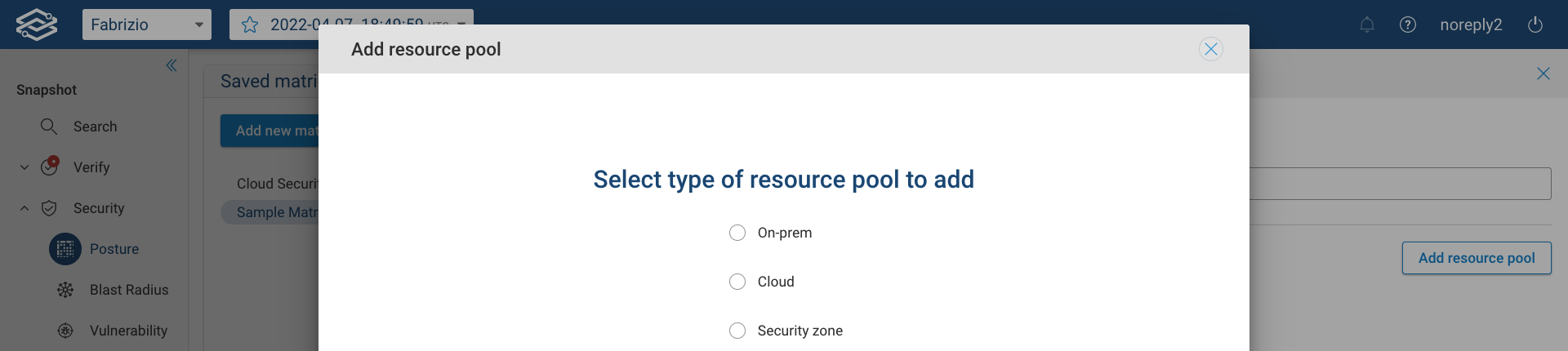
On-prem
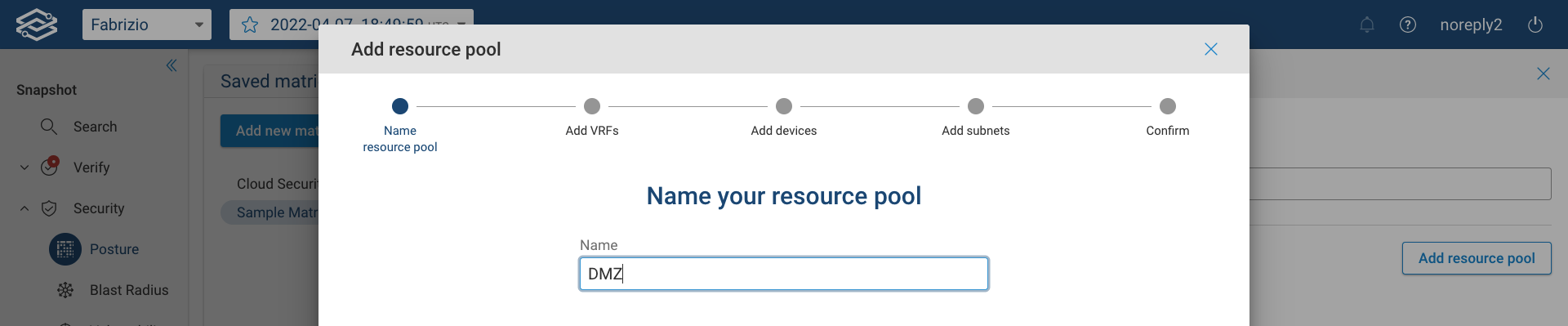
On-prem resource pools can include a combination of VRFs, devices, and subnets.
First, provide a name:
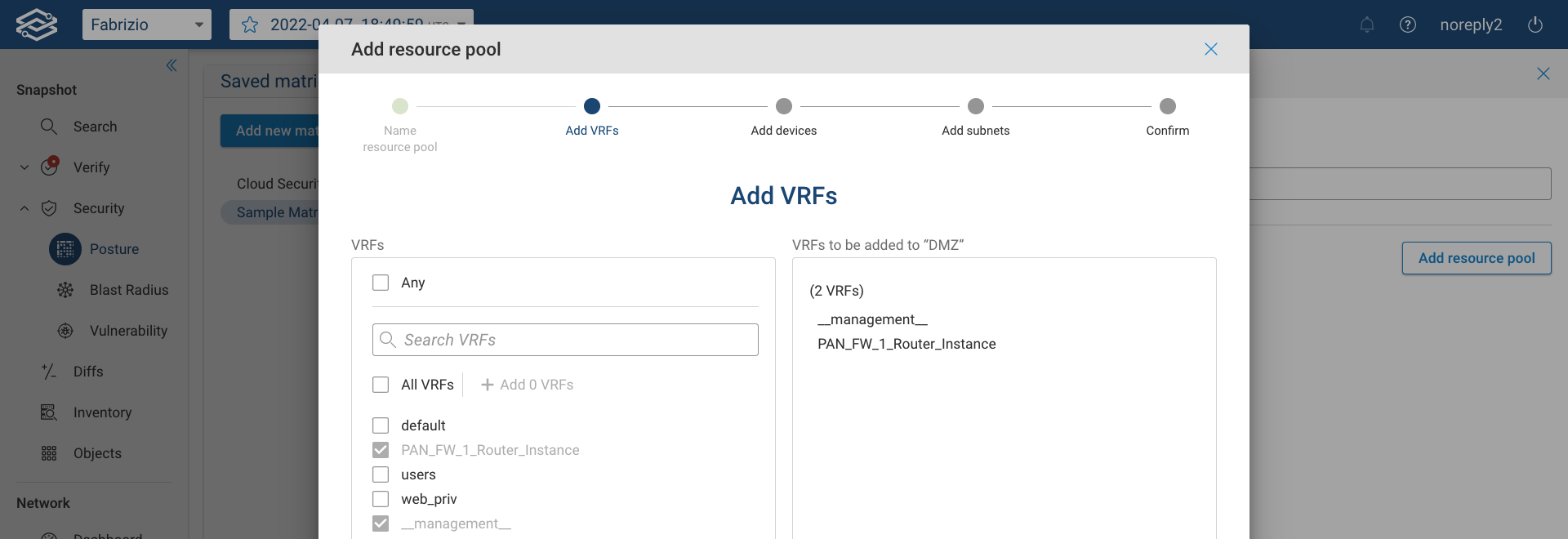
Then add VRFs from the provided VRFs list. All the discovered VRFs are listed, and the search feature allows you to quickly find and add them:
Then add devices from the provided devices list:
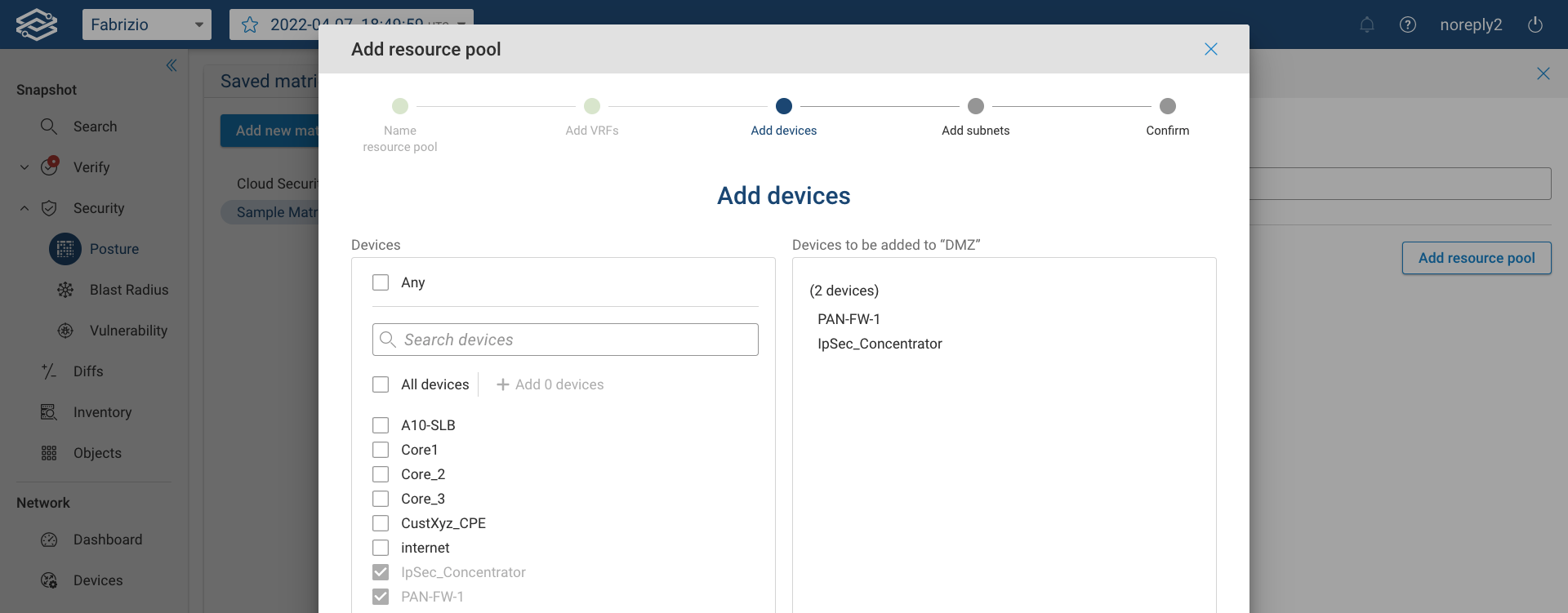
Then add subnets to the resource pool:
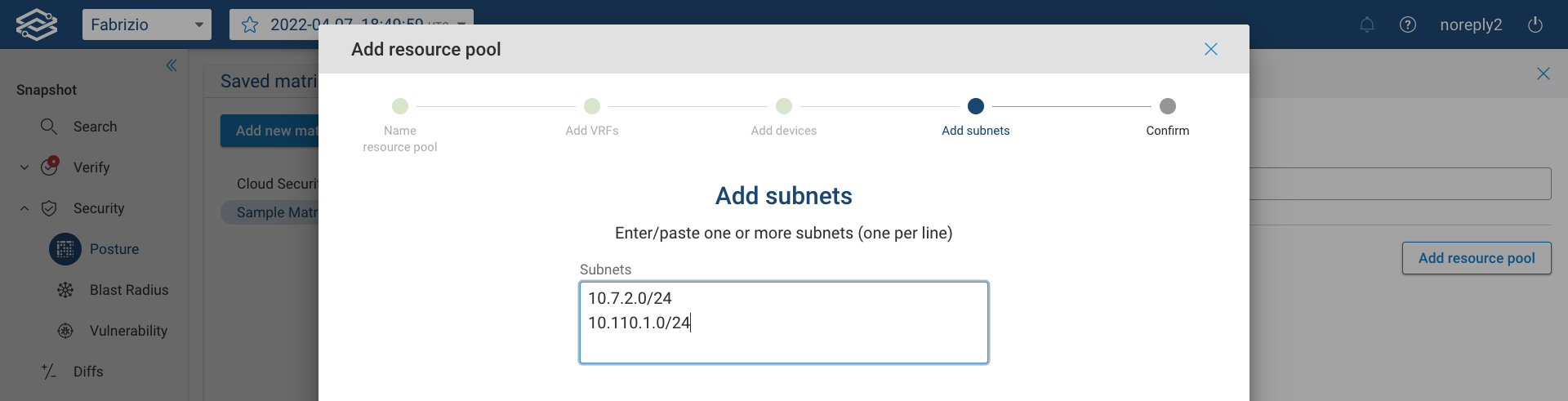
Finally, review the resource pool in the Confirm page and click on Done to complete the process.
Cloud
The second type of resource pool is Cloud.
Cloud resource pools can include a combination of cloud subnets and security groups.
Start by providing a name:
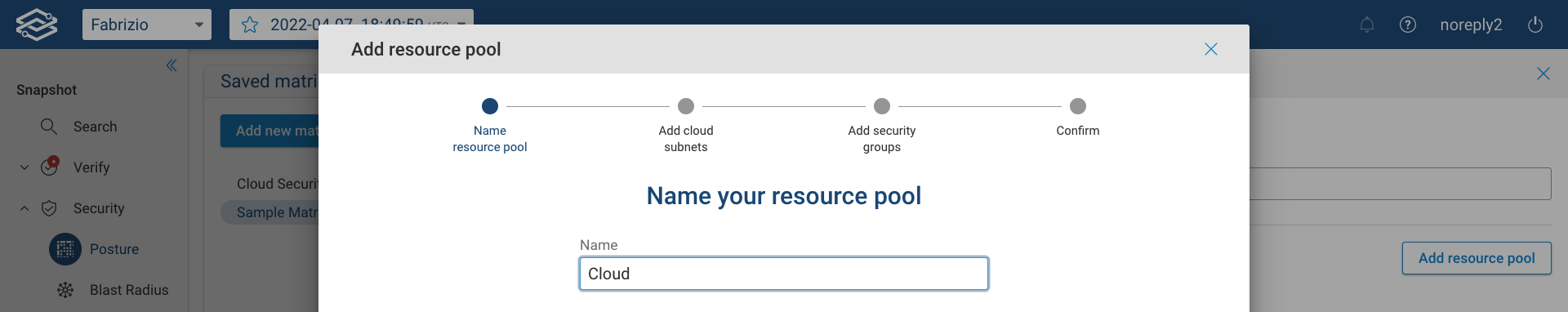
Then add cloud subnets from the provided list:
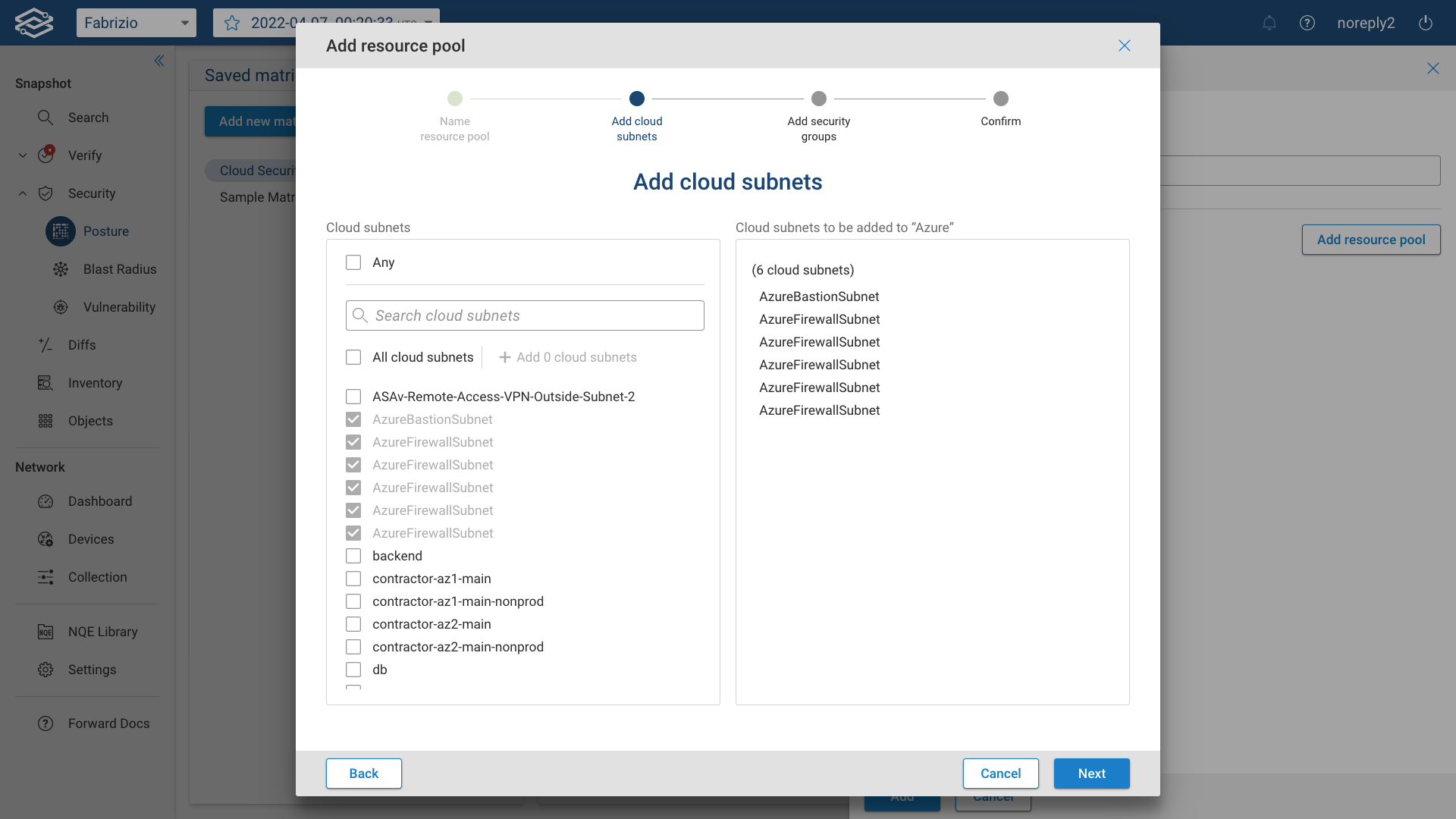
Then add security groups from the provided list:
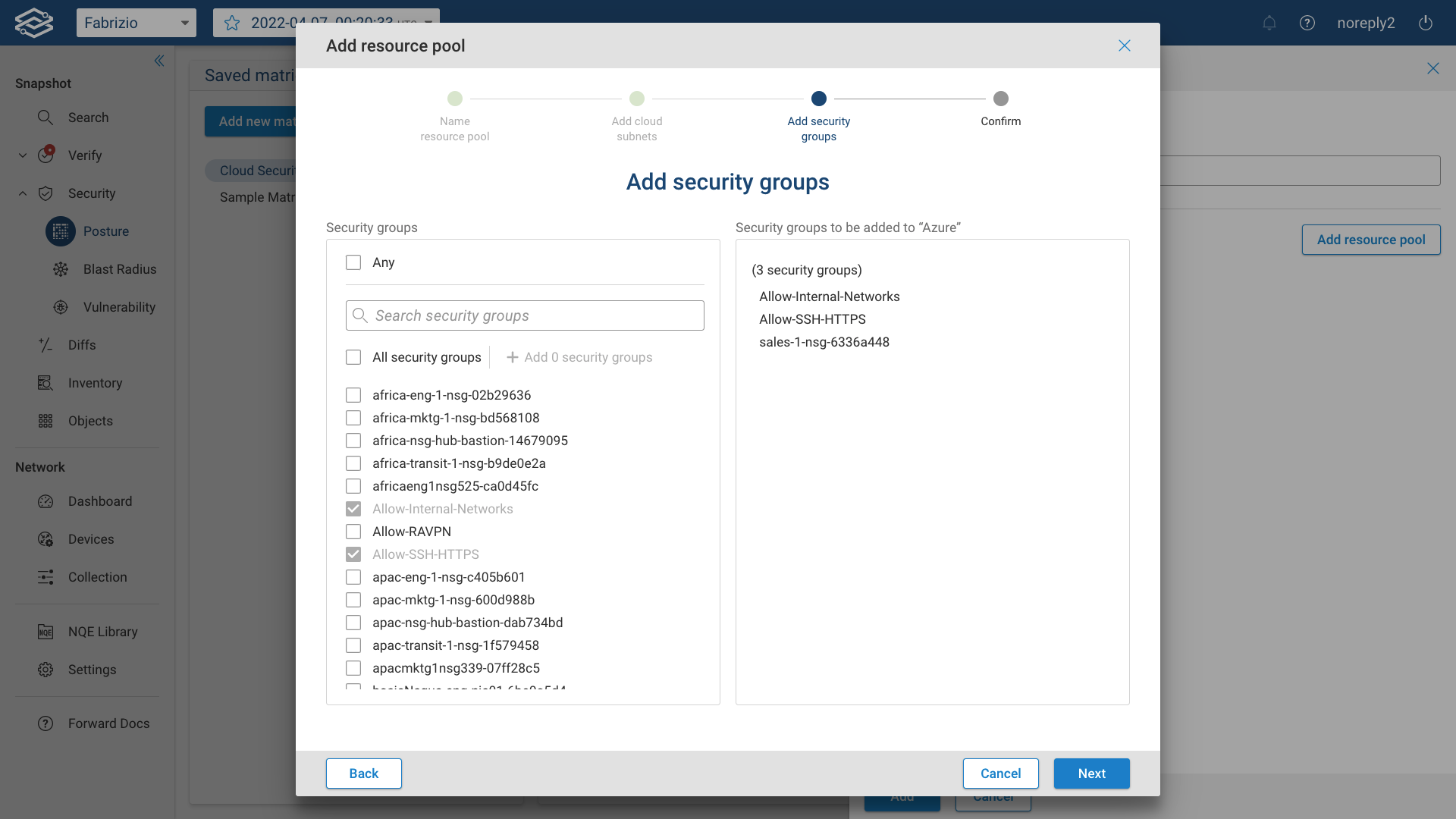
Finally, review the resource pool in the Confirm page and click on Done to complete the process.
Security Zone
Security zones configured in firewalls can be added as well.
First, select the device. All the devices that have zones configured for security will be available in the drop-down menu:
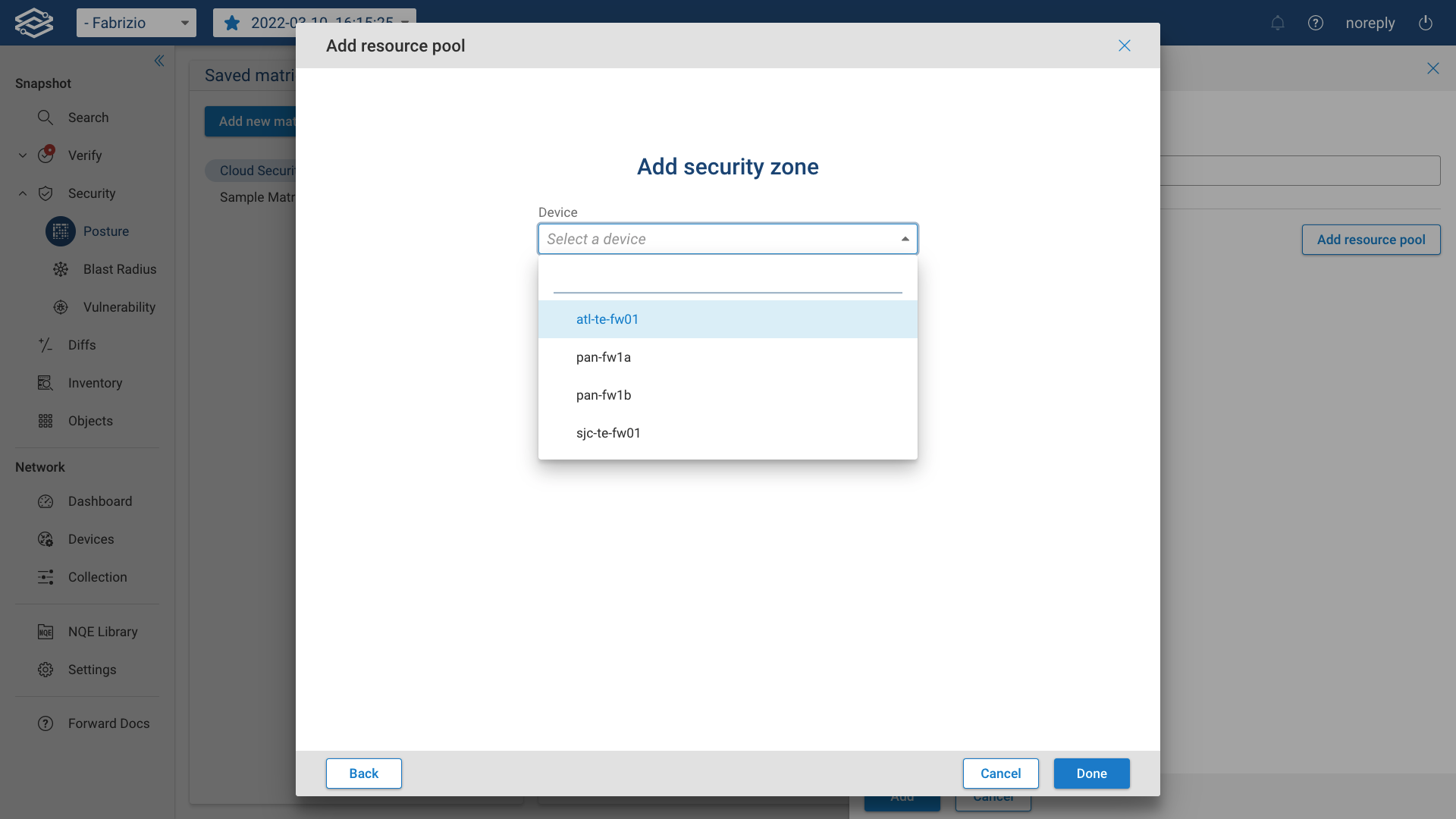
Then, select the security zone. All the detected zones of a selected device will be visible under this drop down menu.
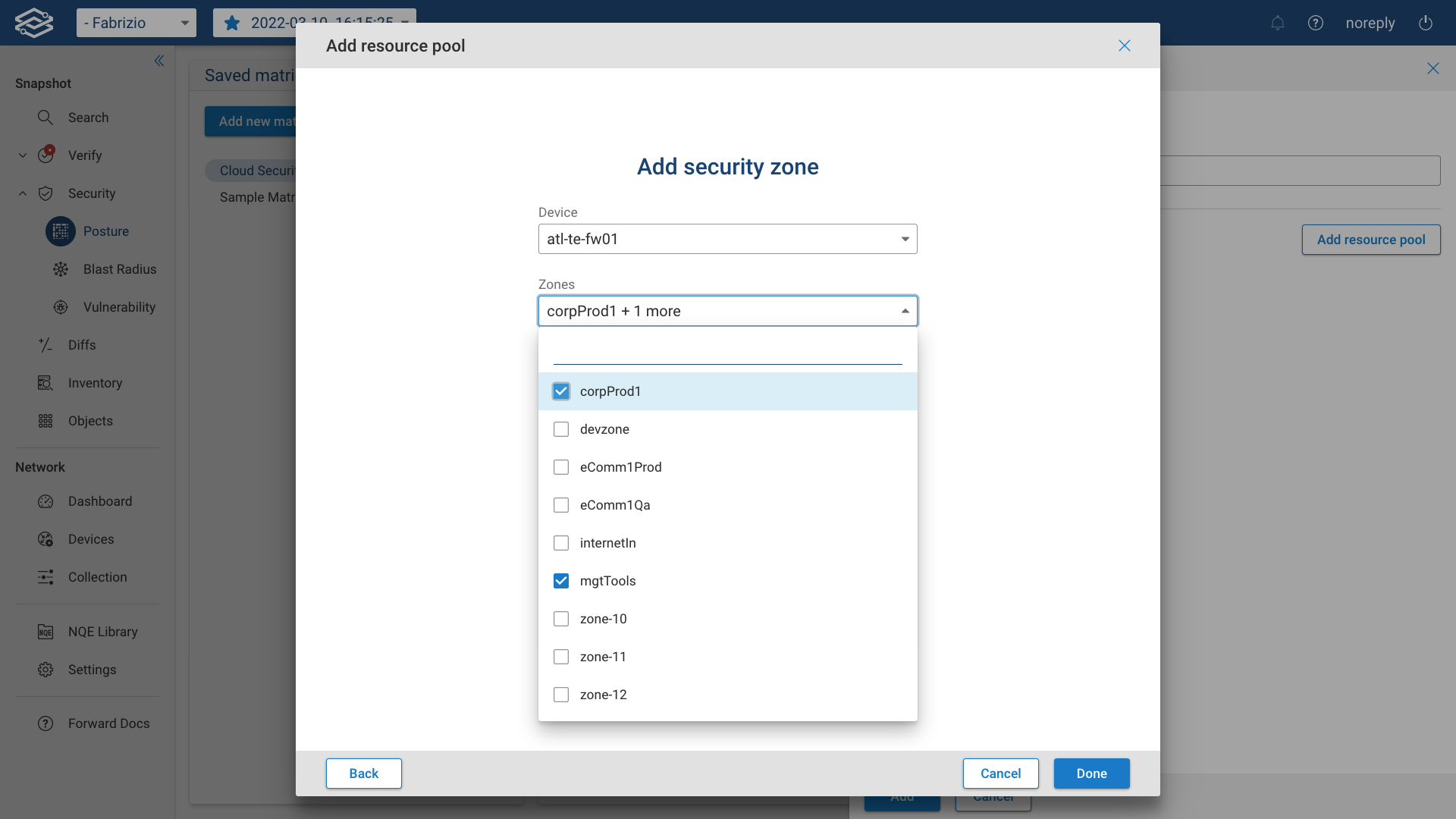
Finally, click on Done to complete the process.
Once all the resource pools are included in the matrix, click the Add button to save it.
Security Posture Analysis
When a matrix filter is selected, Forward Enterprise will present the analysis upon completion of the calculation as shown in the image below:
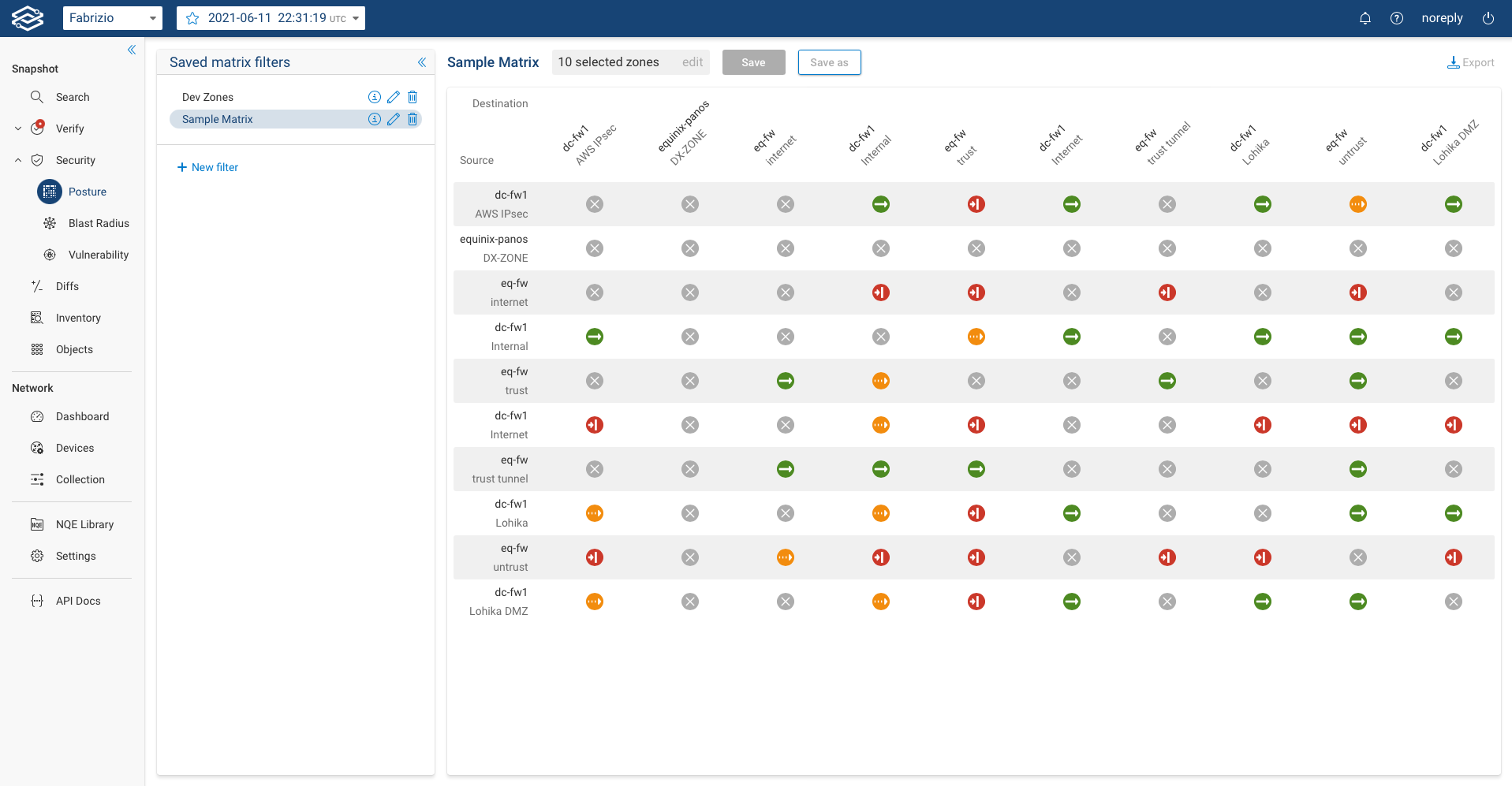
There are four possible statuses:
- Open Connectivity: This status represents that there is an open connectivity from the source zone to the destination zone for all subnets that are routed from the source zone to the destination zone.
- Partial Connectivity: This status represents that there is a connectivity from one zone to another zone however some subnets, protocols or ports are unable to connect from the source zone to the destination zone.
- Blocked by ACL: This status represents that there is no connectivity between any subnet, ports or protocols from the source zone to the destination zone due to an ACL.
- No route: This status represents that there is no connectivity between any subnet, ports or protocols from the source zone to the destination zone due to routing, i.e. traffic is not routed from the source zone to the destination zone for any subnet.
Upon clicking on the icon that represents the connectivity status, users can further evaluate details such as Source IP, Destination IP, Protocol and Ports.
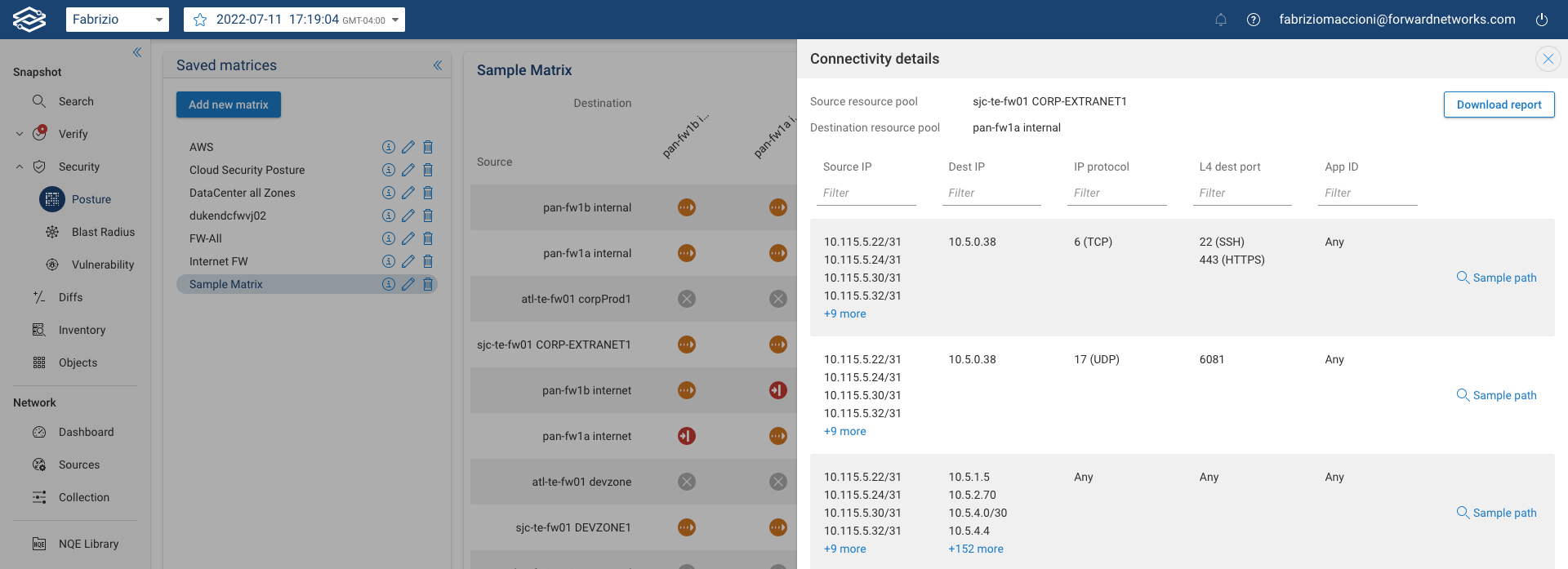
Each row indicates a set of Source IP, Dest IP, IP protocol, L4 dest port, and Layer 7 App ID that have connectivity between the source and destination zone. To view details of the paths taken by sample traffic from that row, click on View sample path to be redirected to the path analysis application.