Vulnerability Analysis
Overview
Network device operating systems can be vulnerable to security flaws. Publicly disclosed vulnerabilities are assigned a CVE (Common Vulnerabilities and Exposures) ID number and a severity level based on their impact. CVEs help IT professionals prioritize and address these vulnerabilities to secure systems and networks.
Networking vendors often fix security vulnerabilities by issuing new OS versions. Therefore, network operators need to evaluate their devices' operating systems regularly. However, the number of vulnerabilities and affected devices can be overwhelming, making it difficult to determine which devices should be updated first.
OS Vulnerability Analysis
To simplify this process, Forward Enterprise provides a network device vulnerability analysis tool. This tool automatically compares CVE information from the vendors and the NIST National Vulnerability Database (NVD) with the OS versions running on your devices, producing a list of possibly affected devices and related vulnerabilities.
CVE Database Updates: The CVE database on Forward SaaS is updated daily. On-premises deployments receive the CVE database with each release but can also update it independently. For more information, see Update CVE database.
Enhanced Vulnerability Analysis
Some vulnerabilities impact devices only if specific configurations are present, specific features are enabled, or the device is deployed in a certain way.
Some vendors, like Cisco, provide detailed descriptions of some CVEs, including required configurations that are vulnerable. This information is available at vendor-specific sites; for example, the Cisco Security Advisories can be found here.
Forward Enterprise's Enhanced Vulnerability Analysis incorporates these descriptions and automatically checks them against device configurations. This helps determine a device's actual vulnerability status, aiding in prioritizing remediation efforts.
Even with enhanced analysis, we always recommend checking the details of the CVE before deciding the next appropriate actions.
The specific list of operating system (OS) versions that include enhanced analysis is available in the Feature Matrix section of the documentation. Forward Enterprise will continue to expand the number of CVEs and vendors in future releases of the Forward vulnerability database.
The following NQE query can be used to retrieve the complete list of device vendors and OSes with enhanced analysis support:
foreach cveDatabase in [network.cveDatabase]
foreach cve in cveDatabase.cves
foreach vendorInfo in cve.vendorInfos
foreach criteria in vendorInfo.criteria
where criteria.osCriteria.dependsOnConfig == true
select distinct{
vendor: vendorInfo.vendor,
criteria.osCriteria.OS
}
Navigating the Vulnerability Analysis Page
To access the Vulnerability Analysis page, navigate to Security → Vulnerability from the left navigation menu.
Each tab within the Vulnerability Analysis page presents key vulnerability metrics, along with two detailed views for CVE-specific information: Devices and CVEs.
The information in both tabs is broken down in different sections as highlighted in the following picture:
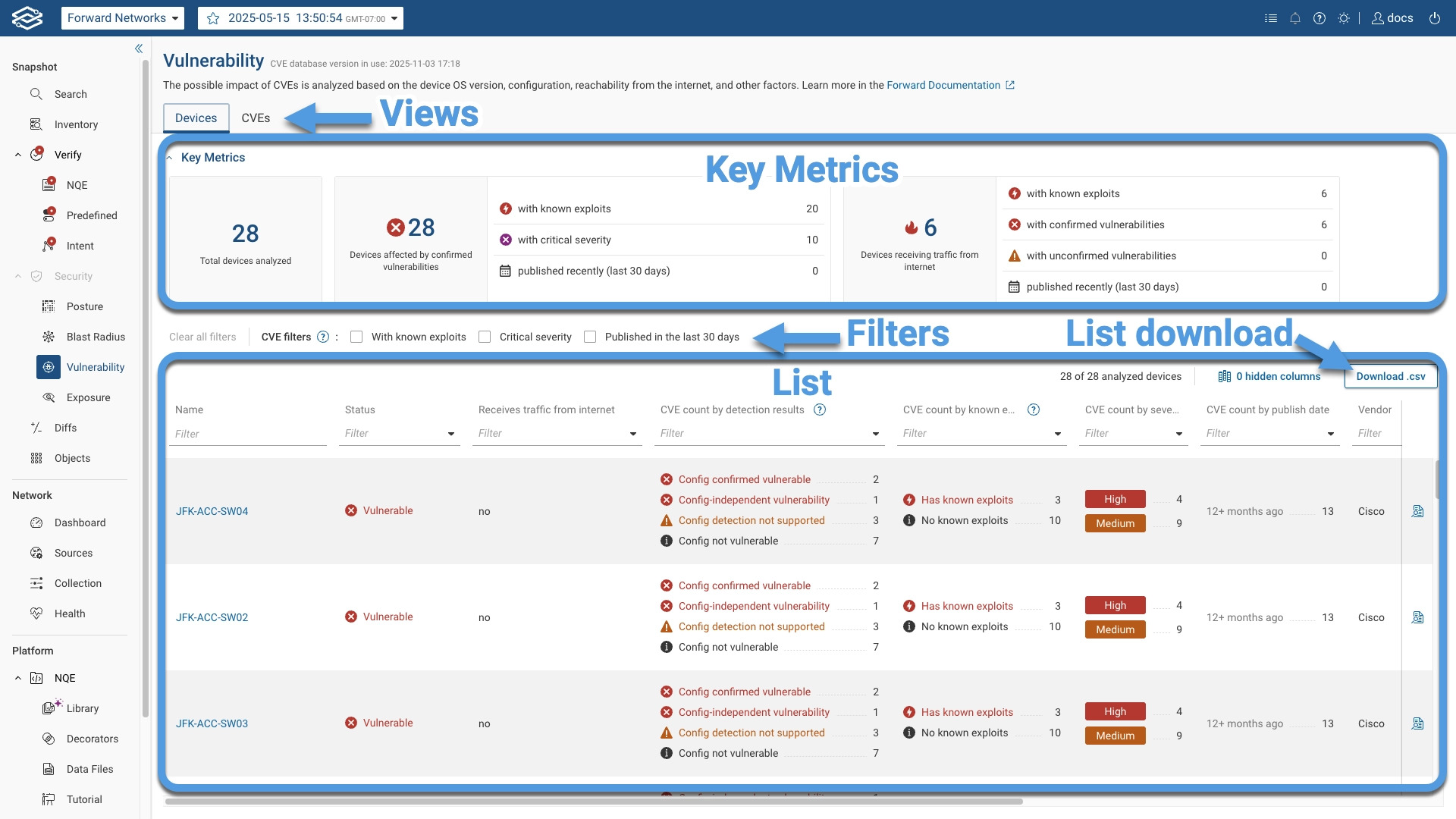
Devices Tab
The Devices tab is the default view when navigating the page. This tab applies a device-centric filter to the vulnerabilities list, focusing on summarizing CVE detection results for each impacted device.
Key metrics are displayed at the top while a filterable list of devices is displyed at the bottom.
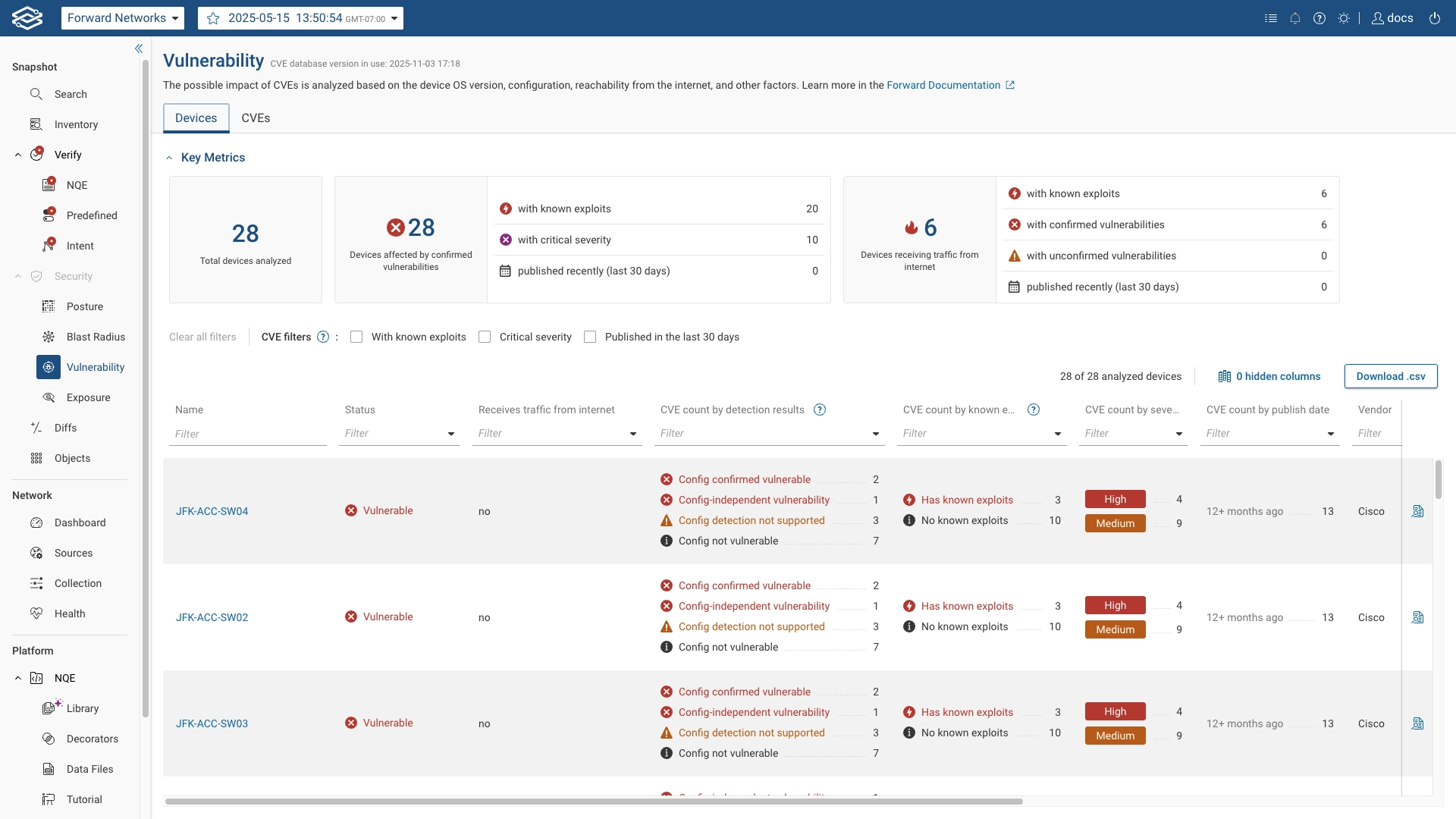
Key Metrics
Key metrics displays numerical counts for device-related vulnerability data:
- Total devices analyzed: Total number of devices where the current OS version is affected by at least one CVE included in the analysis.
- Devices affected by confirmed vulnerabilities: Number of devices confirmed as vulnerable, with counts broken down
by:
- Devices with known exploits
- Devices affected by CVEs with critical severity
- Devices affected by CVEs published recently (last 30 days)
- Devices receiving traffic from internet: Number of devices receiving traffic from internet. Counts are broken down
by:
- Devices with known exploits
- Devices with confirmed vulnerabilities
- Devices with unconfirmed vulnerabilities
- Devices affected by CVEs published recently (last 30 days)
The values above will be zero if the Internet node is not configured.
Clicking any metric applies a filter to the displayed results.
Device List
Each row in the list of devices includes the following details:
- Name: The name of the device. Clicking the device name opens a new browser tab in Search, displaying
additional details about the device for further investigation.
- Status: Displays a summary of the device status based on the currently applied filters:
Vulnerable,Potentially vulnerable,Config not vulnerable. - Receives traffic from internet: Indicates whether the device receives traffic from the Internet, which can impact its vulnerability risk.
- CVE count by detection results: Describes how the CVE was identified on the device. See Detection Results for details on result categories.
- CVE count by known exploits: Shows how many detected CVEs on the device have documented exploits. Filter options include Has known exploits and No known exploits.
- CVE count by severity: Lists the count of severities of the detected CVEs from
CriticaltoLow. - CVE count by publish date: Lists the counts of cves within each age bucket (past 30 days, 1 month to 12 months, older than 1 year).
- Vendor: The vendor of the device.
- OS: The operating system of the device.
- OS Version: The specific OS versions on the device.
- Tags: Tags associated with the impacted devices for easier identification and filtering.
- Location: Assigned location of the device.
Clicking the See details icon opens a drawer with additional information about the selected device.
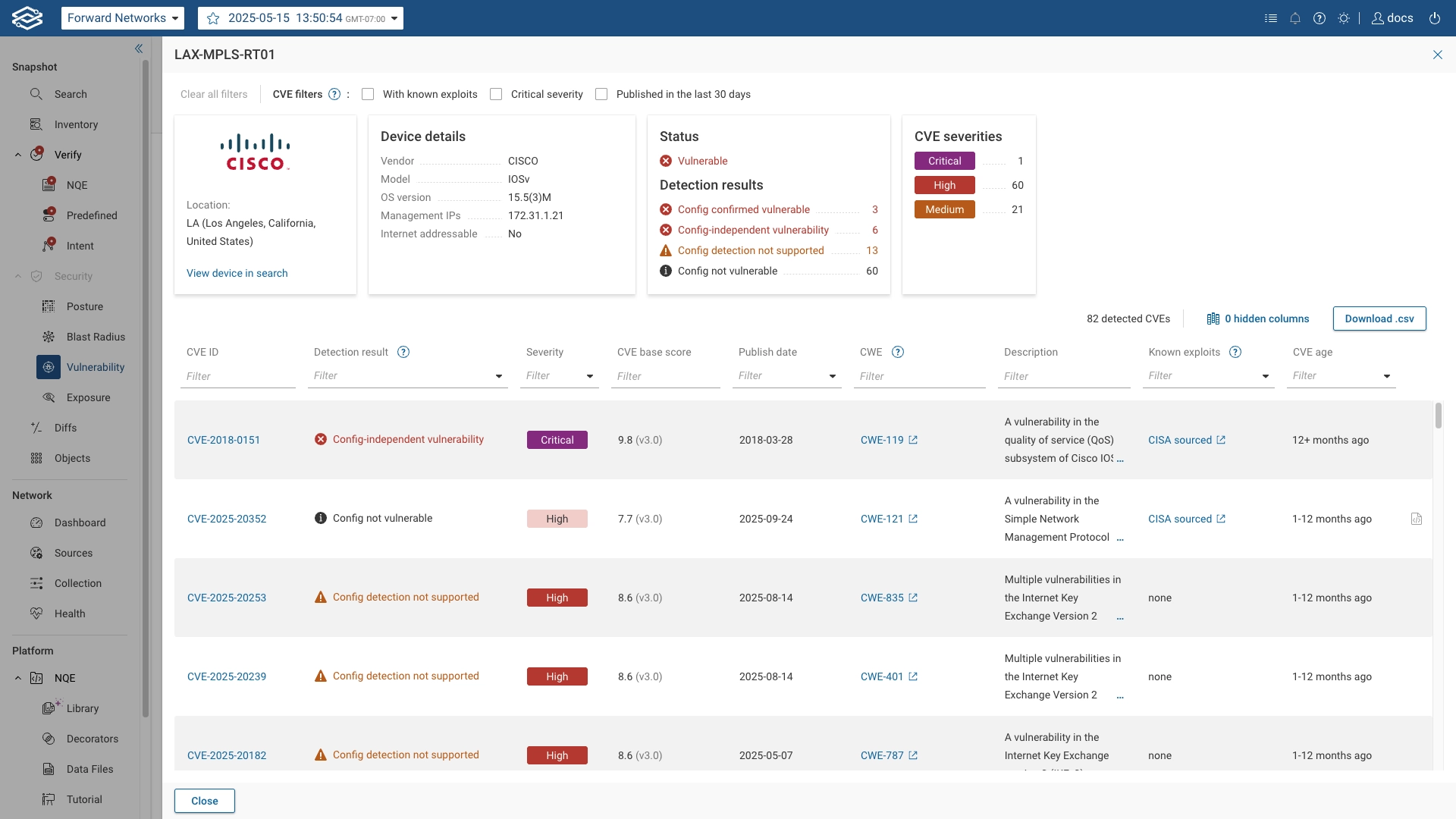
The drawer displays:
- Device details: Displays device-specific information.
- Status: Displays the number of detection results for configs confirmed vulnerable and configs confirmed not vulnerable.
- CVE severities: Displays the count of CVE severities detected on the device, broken into categories: Critical, High, Medium.
The drawer also provides a table of CVEs affecting the device, with the following details for each CVE:
- CVE ID: The unique identifier for each CVE. Clicking this opens detailed CVE information.
- Detection result: Describes how the CVE was identified on the device. See Detection Results for details on result categories.
- Severity: The severity rating of the CVE.
- CVE base score: The CVSS base score of the CVE.
- Published date: The date when the CVE was officially published.
- CWE: Associated CWE identifiers, hyperlinked to the MITRE CWE database.
- Description: A brief description of the CVE and its impact.
- Known Exploits: Shows if the CVE has a published exploit. Entries display the source (CISA or vendor). CISA entries link directly to the CISA Known Exploited Vulnerabilities Catalog.
- CVE age: Displays the age of the CVE.
CVEs Tab
Selecting the CVEs tab applies a CVE-centric filter to the vulnerabilities list.
Key metrics are displayed at the top while a filterable list of CVEs is displyed at the bottom.
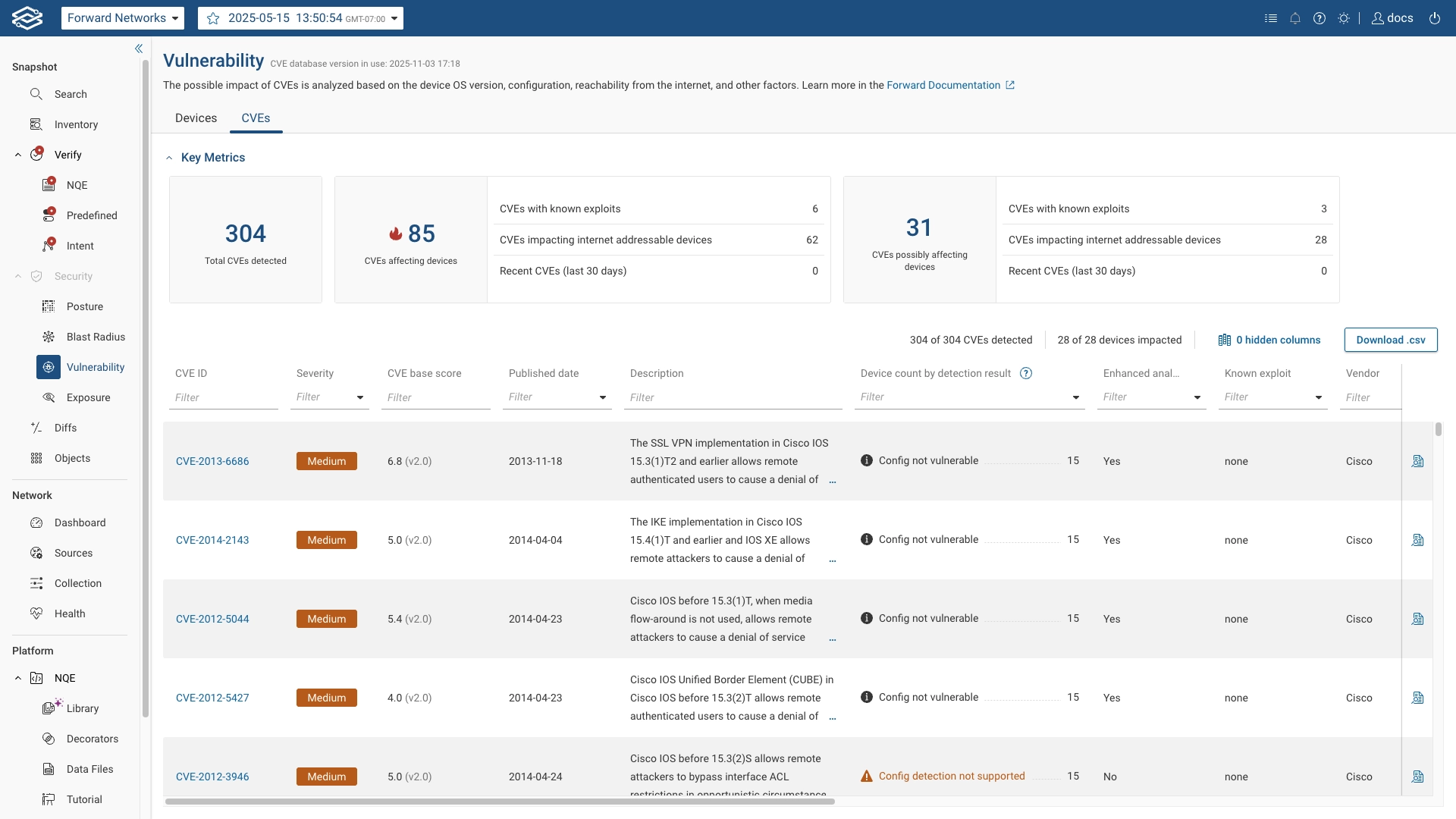
Key Metrics
Key metrics display numerical counts for CVE-related data:
- Total CVEs detected: Overall number of CVEs affecting at least one device in the network.
- confirmed vulnerabilities: Number of CVEs confirmed to impact devices, with counts broken down by:
- CVEs with known exploits
- CVEs affecting devices receiving traffic from the internet
- Recent CVEs (last 30 days)
- CVEs possibly affecting devices: Number of CVEs that may impact devices, but where Enhanced Analysis beyond OS version matching was not performed, with counts broken down by: - CVEs with known exploits - CVEs affecting devices receiving traffic from the internet - Recent CVEs (last 30 days)
CVE List
The CVEs list includes:
- CVE ID: The unique identifier for each CVE. Clicking this opens detailed CVE information.
- Severity: The severity rating of the CVE, indicating how critical the vulnerability is.
- Known exploits: Shows if a CVE has a published exploit. Entries display the source (CISA or vendor). CISA entries link directly to the CISA Known Exploited Vulnerabilities Catalog.
- CVE base score: The base score of the CVE, representing the severity of the vulnerability.
- Published date: The date when the CVE was officially published.
- Description: A brief description of the CVE and its impact.
- Device count by detection result: Describes how the CVE affects devices in the network with corresponding Detection Results counts. See Detection Results for details on result categories.
- Config dependent: True if the CVE depends on a specific device configuration, unknown if enhanced analysis was not performed on the CVE.
- Vendor: The vendor of the devices affected by the CVE.
- OS: The operating system affected by the CVE.
- OS version: The operating system versions affected by the CVE.
- Devices impacted: The number of devices affected by the CVE.
- CVE Base score: CVE CVSS based score for that OS.
- Published date: CVE Published data for that OS.
- Tags on impacted devices: Tags associated with the impacted devices for easier identification and filtering.
- Locations of impacted devices: The assigned location of the impacted devices.
Clicking the View details icon opens a drawer with additional information about the selected CVE. The drawer will display a separate tab for each affected Operating system. In each tab the drawer displays:
- Severity: The severity rating of the CVE.
- CWE classification: Associated CWE identifiers, hyperlinked to the MITRE CWE database.
- CVE base score: The CVSS base score of the CVE.
- Published date: The date when the CVE was officially published.
- Description: A brief description of the CVE and its impact.
- Config dependent: Indicates whether enhanced analysis is supported and CVE is configuration-based.
- Vendor / OS: The vendor and affected operating systems.
- Vendor advisory: A link to the vendor’s published advisory, if available.
- Known Exploits: Shows if the CVE has a published exploit. Entries display the source (CISA or vendor). CISA entries link directly to the CISA Known Exploited Vulnerabilities Catalog.
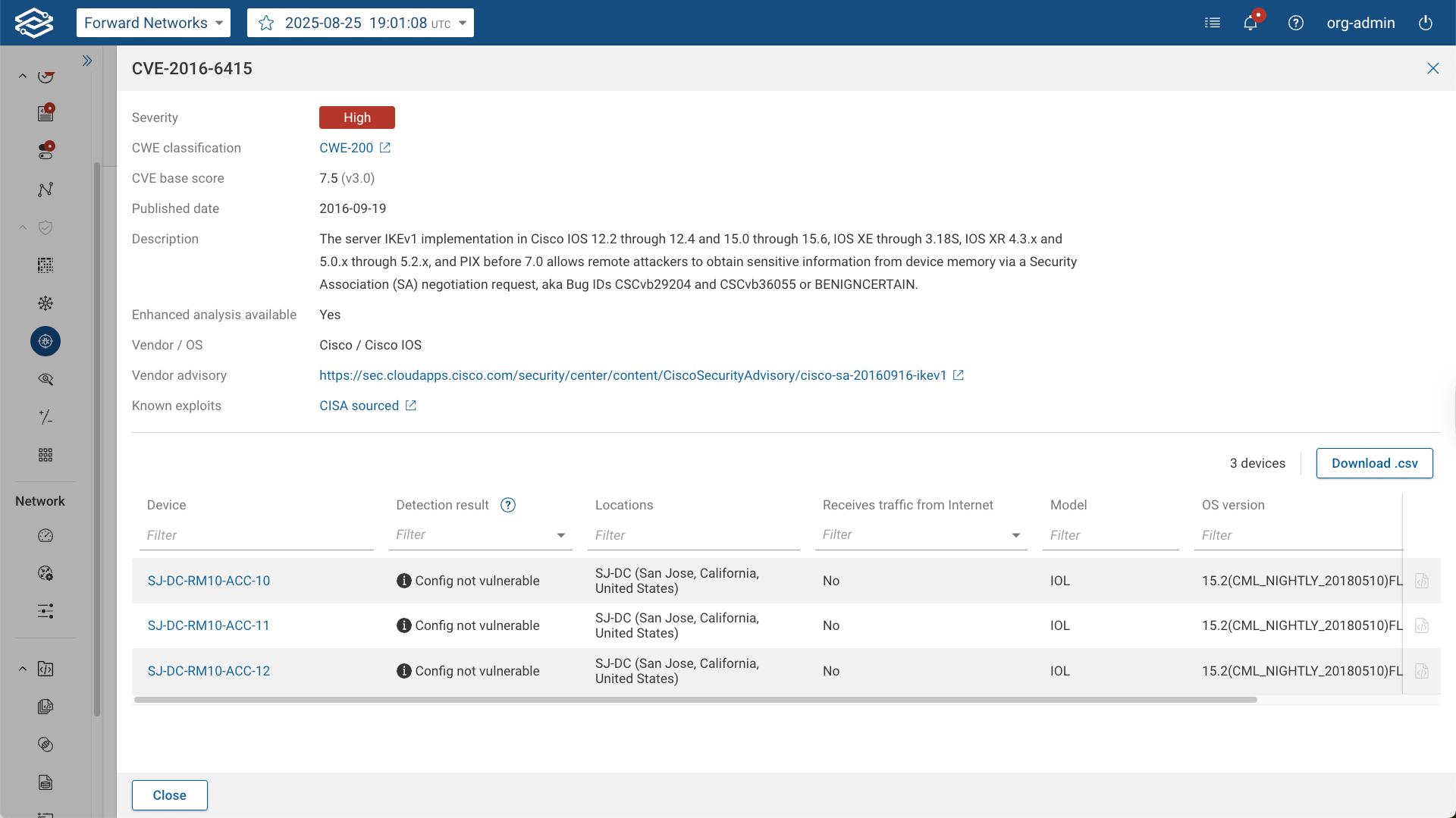
The drawer also provides a table of impacted devices, with the following details for each device:
- Device: The name of the impacted device. Clicking this will provide more detailed information about the device.
- Status: classifies the finding as Vulnerable, Possibly Vulnerable, or Not Vulnerable.
- Detection Result: Describes how the CVE was detected on the device. Configuration icon on the right of the Detection Result opens a drawer highlighting the lines in the device configuration that make this vulnerability exploitable. For CVEs that affect multiple versions of OSes, there are multiple lines (one per OS) for the following columns: Vendor, OS, OS version, Devices impacted, Tags, and Locations. The information in each lines corresponds to the affected devices configured with that Operating System.
- Locations: The assigned location of the impacted devices.
- Receives traffic from Internet: Indicates whether the device receives traffic from the Internet.
- Location: Device location.
- Tags: Device tags.
- Model: The model of the impacted device.
- OS version: The operating system version running on the impacted device.
- Management IPs: The management IP addresses of the impacted device.
Detection Results
The detection result indicates how a device's vulnerability status was determined. Results fall into one of five categories:
| Result | Description | Recommended actions |
|---|---|---|
| The operating system version itself is affected, regardless of configuration. | Apply a patch or up/downgrade to a non-vulnerable OS version. | |
| The OS version is affected, and the device configuration confirms that the CVE is exploitable. | Apply a patch, up/downgrade to a non-vulnerable OS version, or modify the section of the device configuration affecting this CVE. | |
| The OS version is affected, but configuration-based detection is not yet supported for this CVE. | If possible, apply a patch; analyze the device configuration manually to see if a configuration work-around is possible. | |
| The OS version is affected, but Forward could not confirm whether the configuration makes the device vulnerable. | Recheck this device after the next snapshot. If the error persists, report a bug to Forward and apply a patch if possible. | |
| A CVE is reported against this OS version, but the configuration required for the device to be vulnerable is not present. In this case, the OS may contain the vulnerability, but the device’s configuration prevents exploitation. Devices that are not vulnerable at the platform level do not appear in the Vulnerability Analysis application. | Plan to upgrade the device OS during a regular maintenance window. |
In the UI, results are color-coded by severity:
Vulnerable (red)
Potentially Vulnerable (orange)
Not Vulnerable (black)
CVE Search
To search for a CVE, enter the CVE ID in the vulnerabilities table. The search can result in:
- At least one device is affected by the vulnerability.
- CVE-ID does not affect any device supported by Forward Enterprise
- The CVE ID is not present in the Forward CVE database (it may be outdated, irrelevant to supported vendors, or outside the date range included).
CVE Database Update
On Forward SaaS, the CVE database is updated daily. For on-premises deployments, the CVE database is updated with each Forward Enterprise release but can be updated anytime.
The list of CVEs Forward Networks considers may not include hardware vulnerabilities or older CVEs that were not created or updated after January 1st, 2014.
Update via the Forward Enterprise GUI
- Download the latest CVE database from the CVE Update page.
- Navigate to Security > Vulnerability from the left navigation menu.
- Click Update CVE database (top right corner) to upload the CVE database. Optionally, enter the Checksum to verify the file's integrity.
- Click Update.
Update via the Forward Enterprise REST APIs
- Download the CVE Database: Any user with Org Admin privileges can download the latest CVE database from
Forward Software Central using the Forward REST APIs via
GET /api/cve-index. It returns the CVE database as a gzipped binary (.bin.gz) file. - Update the CVE Database: A user with Org Admin privileges can update the CVE database using the Forward REST
APIs via
PUT /api/cve-index.
For detailed instructions, see the REST API docs.