Intent Verification
Overview of Intent Verification
Intent Verification is a crucial feature for ensuring network reliability and security. It focuses on proactive network behavior monitoring by automating the verification of network reachability and compliance with intended policies across the enterprise. This feature allows for the setup of continuous checks that alert you to any discrepancies or policy violations, maintaining the network's operation in line with its intended design.
Estimated Completion Time
10 minutes
Exercise and Steps
Exercise 1: Create and Display Intent Verifications
Objective: Utilize the knowledge from Exercise 3 in Path Search to create an Existential Intent Verification. This aims to validate network behavior against specified intents to ensure network reliability and security.
-
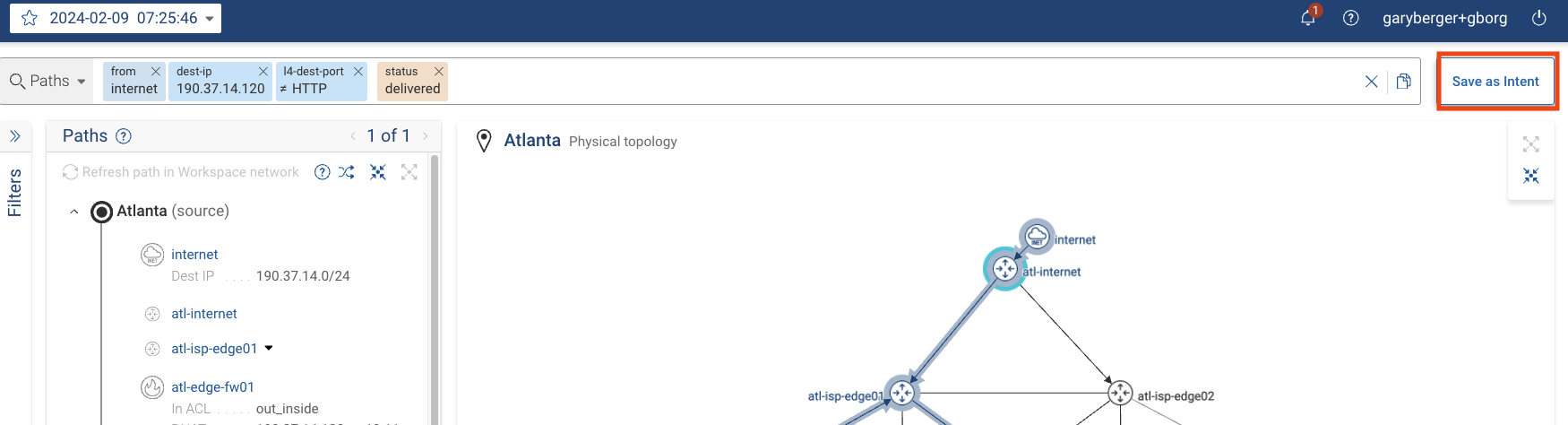
Verification Development: Craft a verification check to identify all network flows originating from the Internet and directed to
190.37.14.120, excluding those using theHTTPSprotocol.f(internet)(ipv4_dst.190.37.14.120)(!tp_dst.HTTP)z(delivered) -
Action: Save as Intent
-
Display Intent Verifications using Verify Application
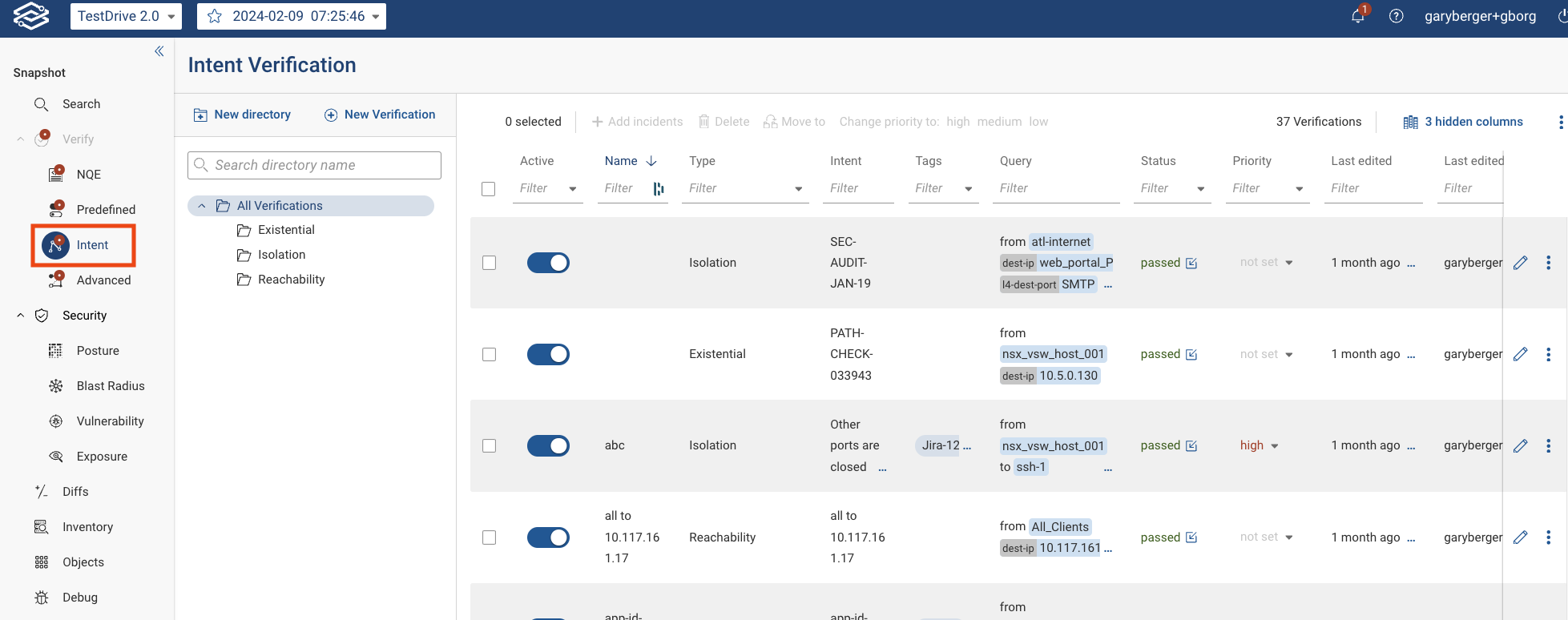
Inquiry: Consider whether this verification will succeed or fail and its implications on network security and policy compliance.
Key Insights
- User-Friendly Transition: The shift from understanding path search semantics to creating verification checks is seamless, highlighting the user-friendly aspect of Intent Verification.
- Proactive Surveillance: Enables proactive monitoring to ensure network compliance and reliability, moving beyond simple reactive measures.
- Streamlined Verification: Automates the process of network verification, conducting continuous checks against defined intents, which is vital for maintaining network integrity.
- Security Enhancement: By verifying network behavior against specific security intents, it helps in identifying vulnerabilities and enforcing security policies more effectively.
- Operational Streamlining: The capability to quickly identify discrepancies or violations improves network operations, reducing the reliance on extensive manual inspections.