Vulnerability Analysis
Overview of the Vulnerability Analysis Exercise
Forward Enterprise offers a detailed analysis of network device vulnerabilities, leveraging information from the NIST CVE index. This exercise guides you through the process of identifying, assessing, and prioritizing vulnerabilities within your network infrastructure.
Estimated Completion Time
15 minutes
Exercise 1: Identifying Vulnerabilities
Objective: Utilize Forward Enterprise to identify vulnerabilities in network devices based on the NIST CVE index. This initial step is crucial for understanding the security landscape of your network. Vulnerabilities are presented in two view options: Devices & CVEs centric.
-
Select Vulnerability Application under Security
-
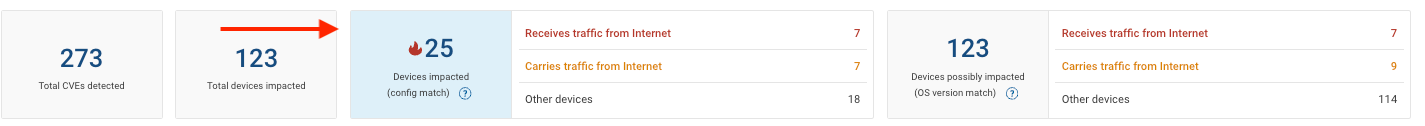
Filter by Devices Impacted (Config Match)
-
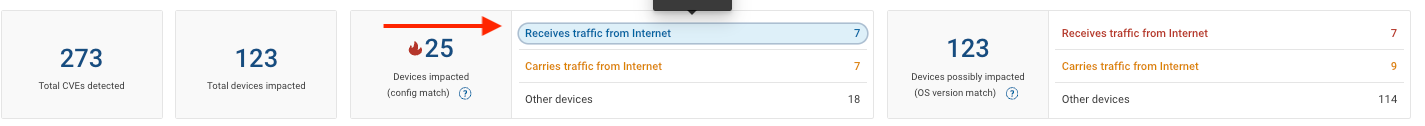
Filter Devices by Interrnet Reachability
-
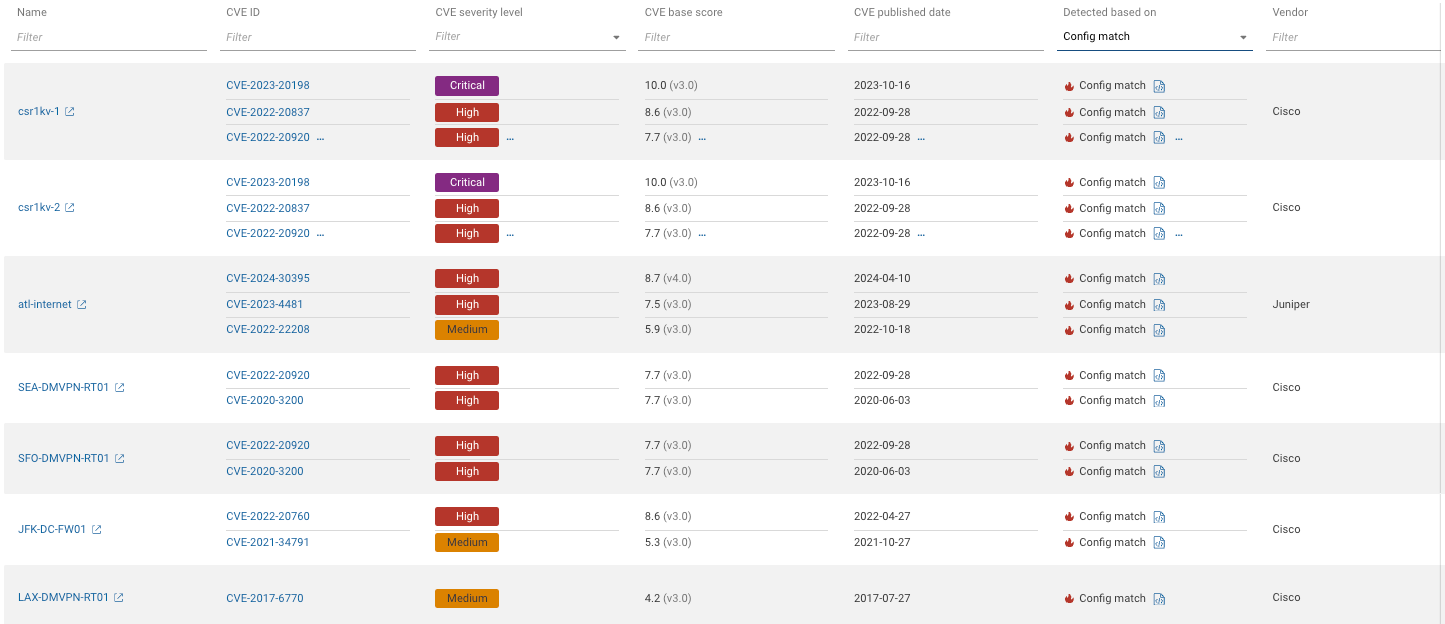
Review prioritized vulnerable devices
Key Insights
- Comprehensive Vulnerability Analysis: Forward Enterprise enables a thorough analysis of network device vulnerabilities, providing insights into potential security risks.
- Prioritization of Remediation Efforts: By assessing the priority and exploitability of vulnerabilities, you can effectively allocate resources towards mitigating the most critical risks first.
- Enhanced Network Security: Understanding and addressing vulnerabilities based on their real-world exploitability helps in strengthening the overall security posture of your network.